Immediately after finding these vulnerabilities, we contacted Tinder via their responsible disclosure program and started working with them.
Consequently, there is a potential risk for up to 685 million users.
It’s a good idea to change your password ASAP.

In DOM-based XSS, the HTML source code and response of the attack will be exactly the same.
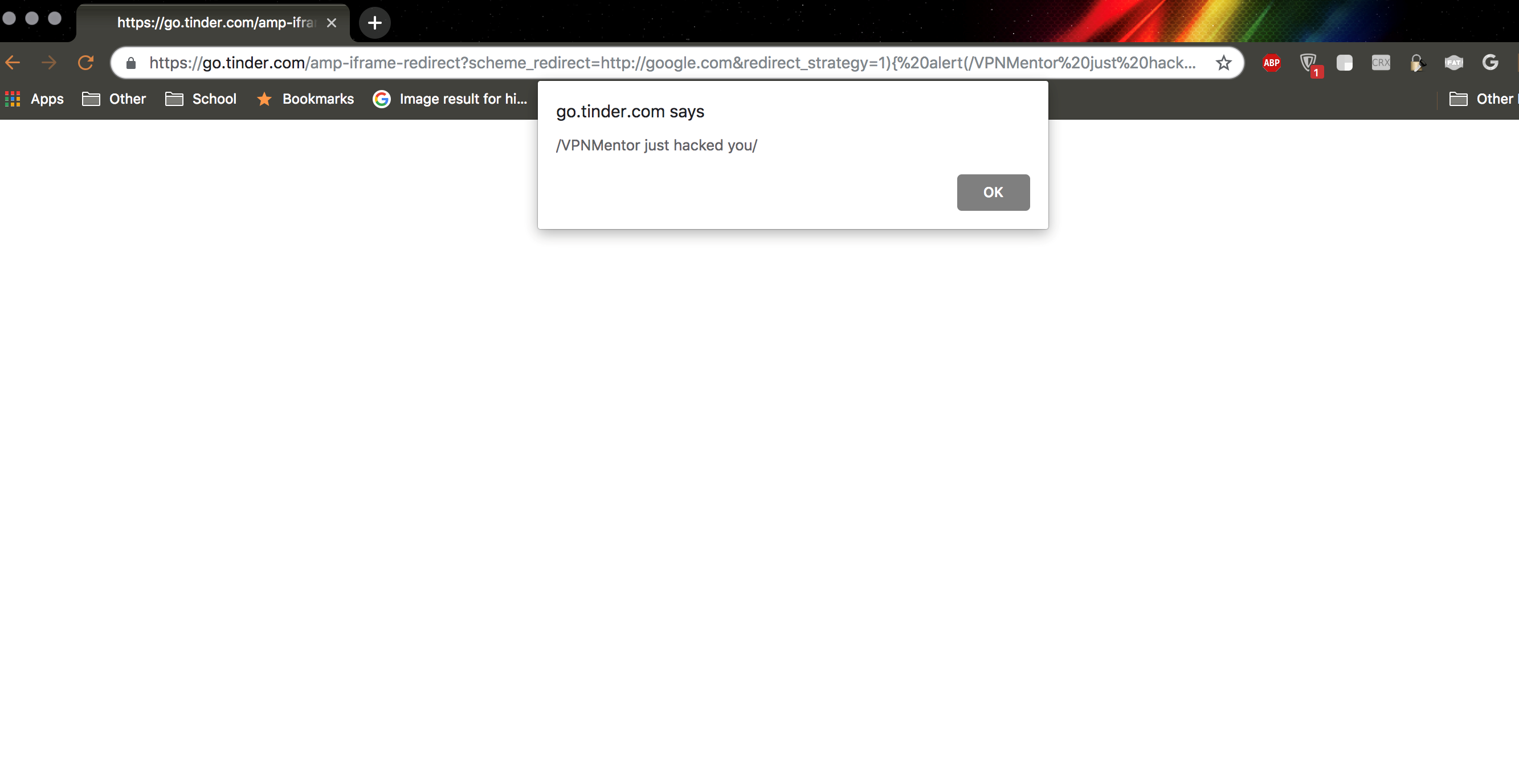
Can you spot the vulnerabilities?
This meant that by modifying redirect strategy to a specially crafted payload to manipulate the DOM.
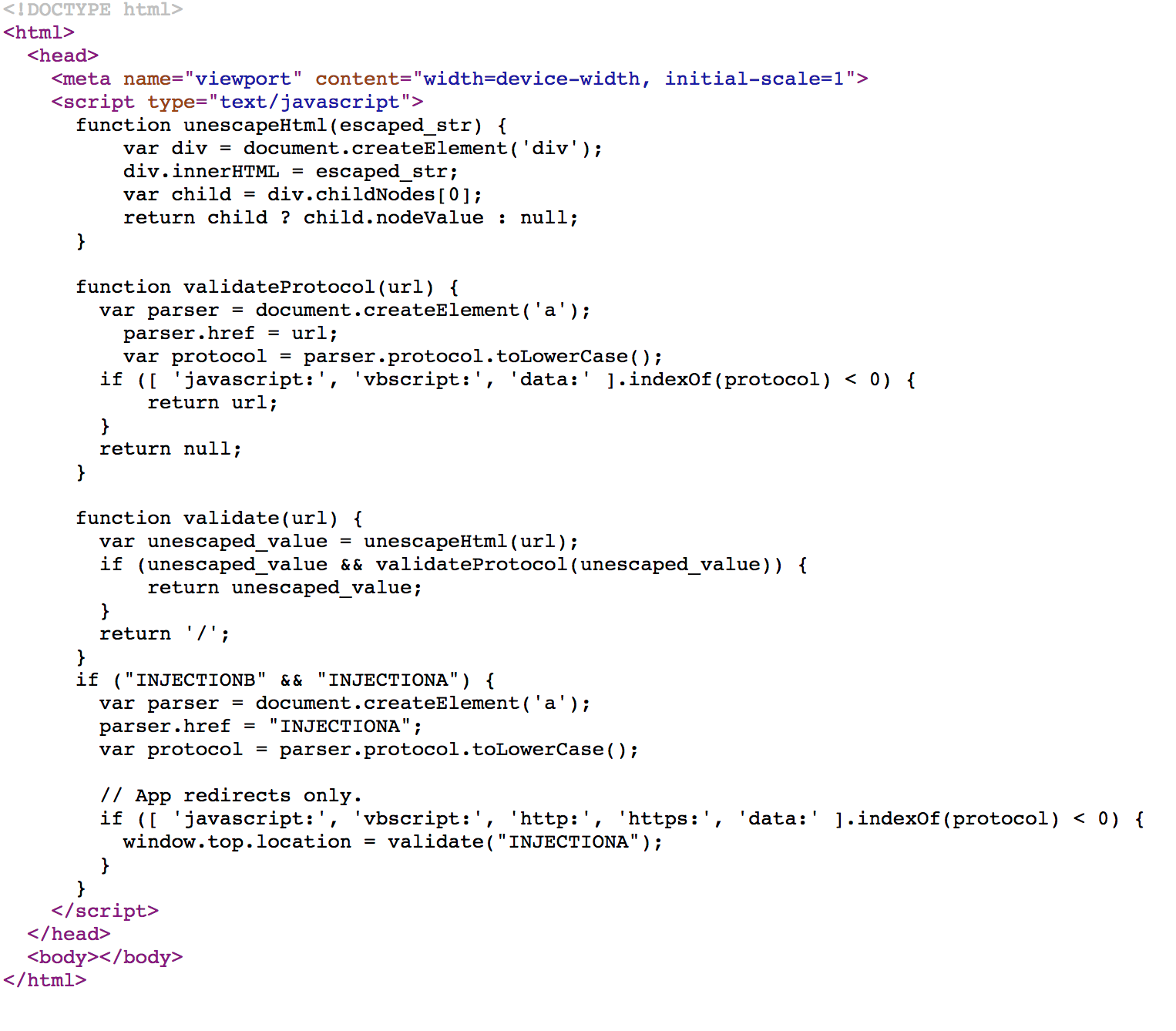
redirect_strategy is INJECTIONA and scheme_redirect is INJECTIONB from the code above.
This method returns -1 if the value to search for never occurs.
go.tinder.com is an alias for custom.bnc.lt, a Branch.io resource.

And many other companies have their alias pointing to it.