Concern about online anonymity stretches well beyond identity theft.
Said another way: this isnt just another how to protect yourself online guide.
We will also explain the critical difference between privacy and anonymity.

Think of this distinction: privacy applies to actions and anonymity applies to your identity.
And how doable is it?
Our guide explains:
How Hackers Get Your Info?

Films and TV shows (looking at you, Mr.
When an app or a website leveragesactual 256-bit encryption: its unbreakable.
In short: the encryption standards arent to blame.

Its whenthey arent properly implementedthat users suddenly find their personal data has been leaked.
In truth: hackers arent all that remarkable.
From the perspective of protecting your anonymity: it remains a user beware world.

Some companies are better than others at safeguarding your data.
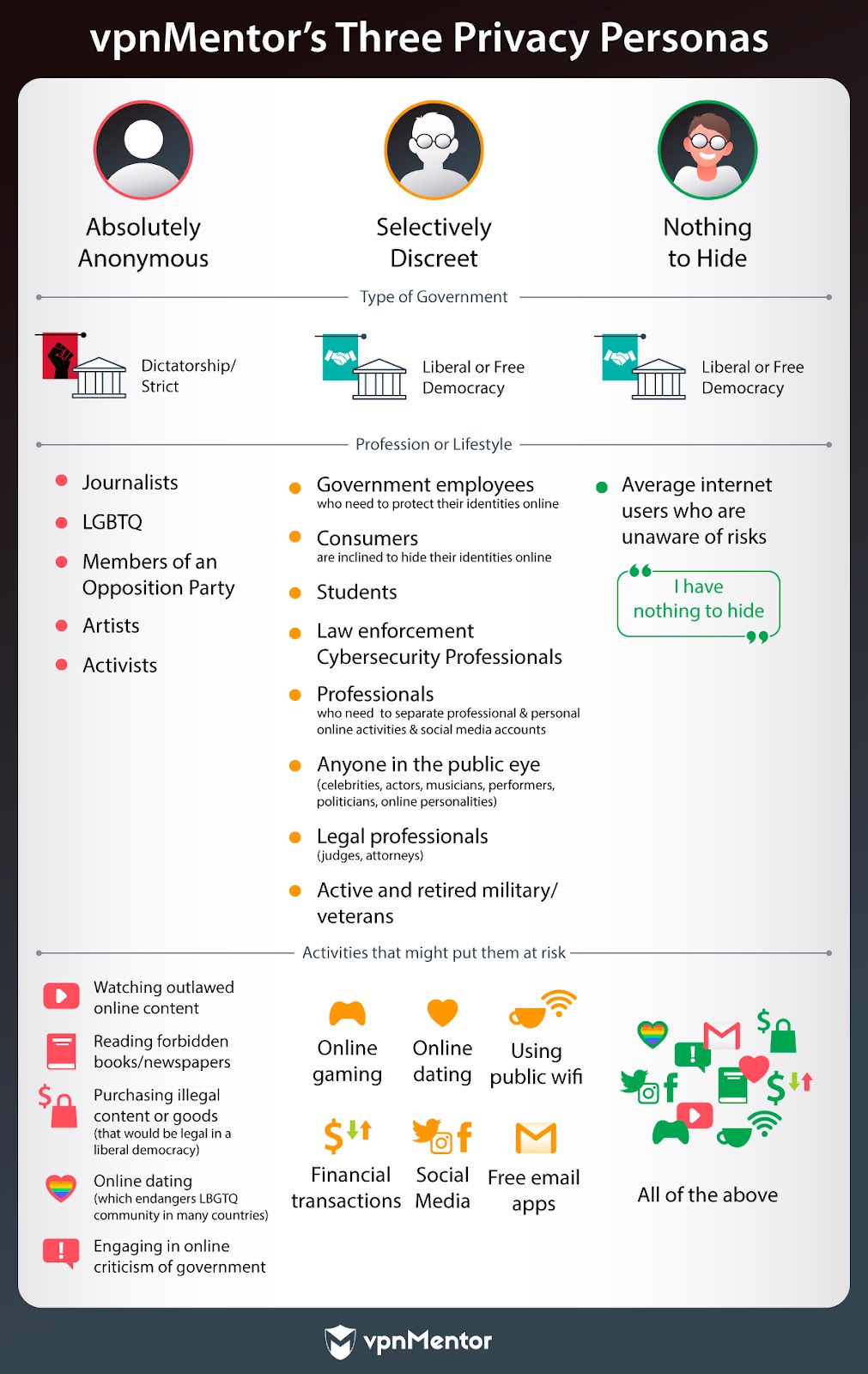
Governments and Privacy: Who is the Strictest?
Becoming the victim of cybertheft is one thing, and something we all need to be careful to avoid.

Arrest and the loss of your freedom and personhood is quite another.
How Strict is Strict?
Anything that harms the nations honor and interests.

If that all sounds vague: thats the point.
In 2006, aHarvard research studyreported that China blocked as many as 18,000 websites.
Currently, even popular websites and apps like Google and Facebook are blocked.

Chinese authorities are particularly punitive when it comes to the possession of pornographic materials.
Possession of porn could lead to athree-year prison sentence.
In 2010, over 5,000 people were arrested in China in relation to shutting downover 60,000 pornographic websites.

The Chinese government has already made it impossible for online tech and privacy to thrive together.
Its Open Net initiative requires that internet service providers (ISPs) send all traffic through state-controlled gateways.
Check out ouronline censorship reportwhich covers Irans troubling censorship patterns.
Charting the vast overreach of the Iranian government and its vast censorship of online content is a full-time job.
In short: anything.
It remains a country where it is truly dangerous to express yourself.

Same-sex relations (homosexuality) is criminalized.
Transgender people are often arrested and fined.
Russia seems bent on surpassing China as the country with the heaviest hand in controlling and censoring web traffic.
With internet censorshipon the rise, that poses an even greater threat to journalists andcritics of the government.
Think of privacy as the various measures that encrypt and hide your actions on the internet.
Staying anonymous on the internet doesnt just mean simply blocking your keystrokes from a web phisher or your ISP.

There are other reasons beyond law enforcement for governments to know your real identity.
you oughta exercise your right to vote, local jurisdictions need the ability to assemble juries and so forth.
Because they are legally obligated to persecute fraud, to verify individual identity, and more.
We are NEVER suggesting that you remotely make any attempts at executing identity fraud.
Rather, identify opportunities for legal anonymity.
Take advantage of when and how you could conceal your identity.
Find the balance between utter transparency and complete (and nearly impossible) secrecy.
That, however, is changing.
Increasingly, more of us are aware of the threats to both our privacy and identities online.

Even if youre not doing anything you dont want anyone to know, your privacy should be your choice.
Innovation was–and is–exciting.
It was exciting to encourage Yahoo to personalize your news feed based on your location.

In this chilling essay for the New York Times, Swisher asks readers to be paranoid about privacy.
The tools that are in place to do this have been with us for a long time.
In the right hands: they are mostly harmless.

Cookies are a key ingredient in the webs personalization revolution.
Session cookies are not inherently dangerous.
Persistent cookies, however, are more troublesome.

Websites sometimes set persistent cookies that sit inside your internet tool and record secure data.
As with cookies, javascript alone isnt the problem.
The problem is that you dont have any control over a third partys web security.

Its the largest report like it ever to be compiled by a news organization.
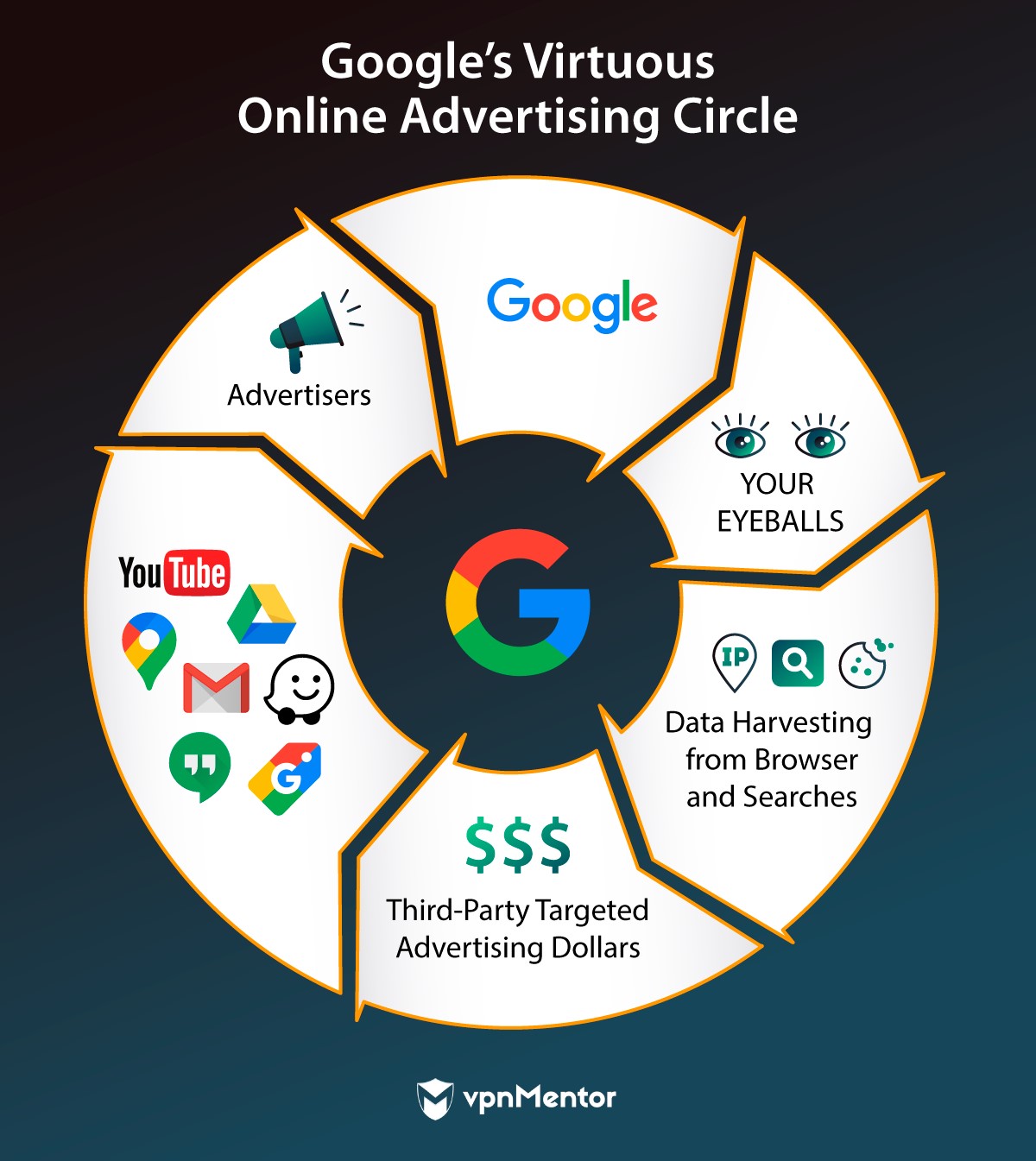
What Does Your ISP Know?
ISPs in America were previously prohibited by law from collecting information about you.

They can sell your information for a profit.
When you sign up for your internet service, you are going to have to share some personal information.
Many of those free services turn your eyeballs into profit.

Its not at all cynical to say that the large free services rent your eyeballs to advertisers.
Then theres also the threat posed by massive data breaches, likethe massive scandal that plagued Yahoo.
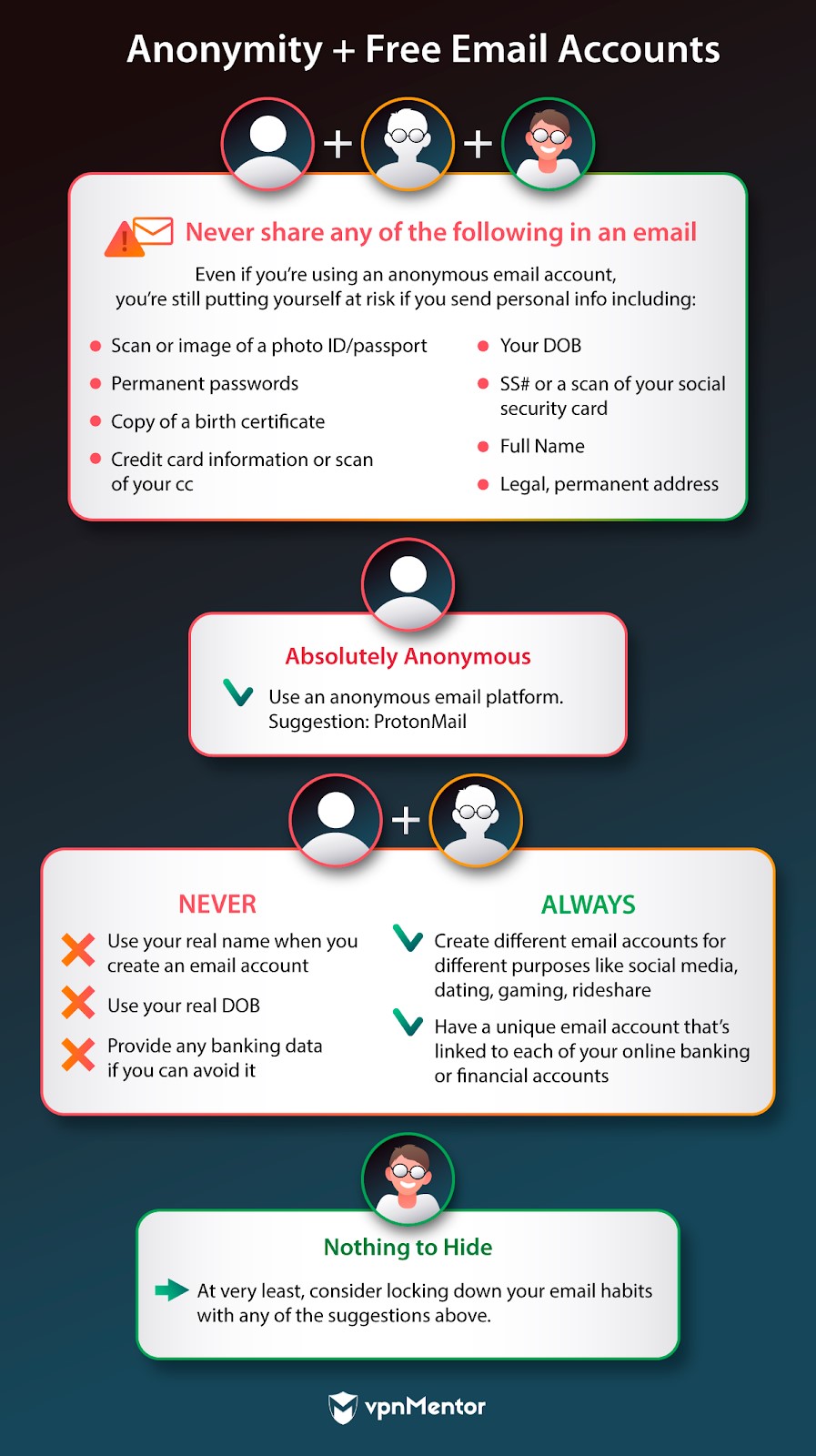
For many reasons: those online email servicesdont need to know the real you.
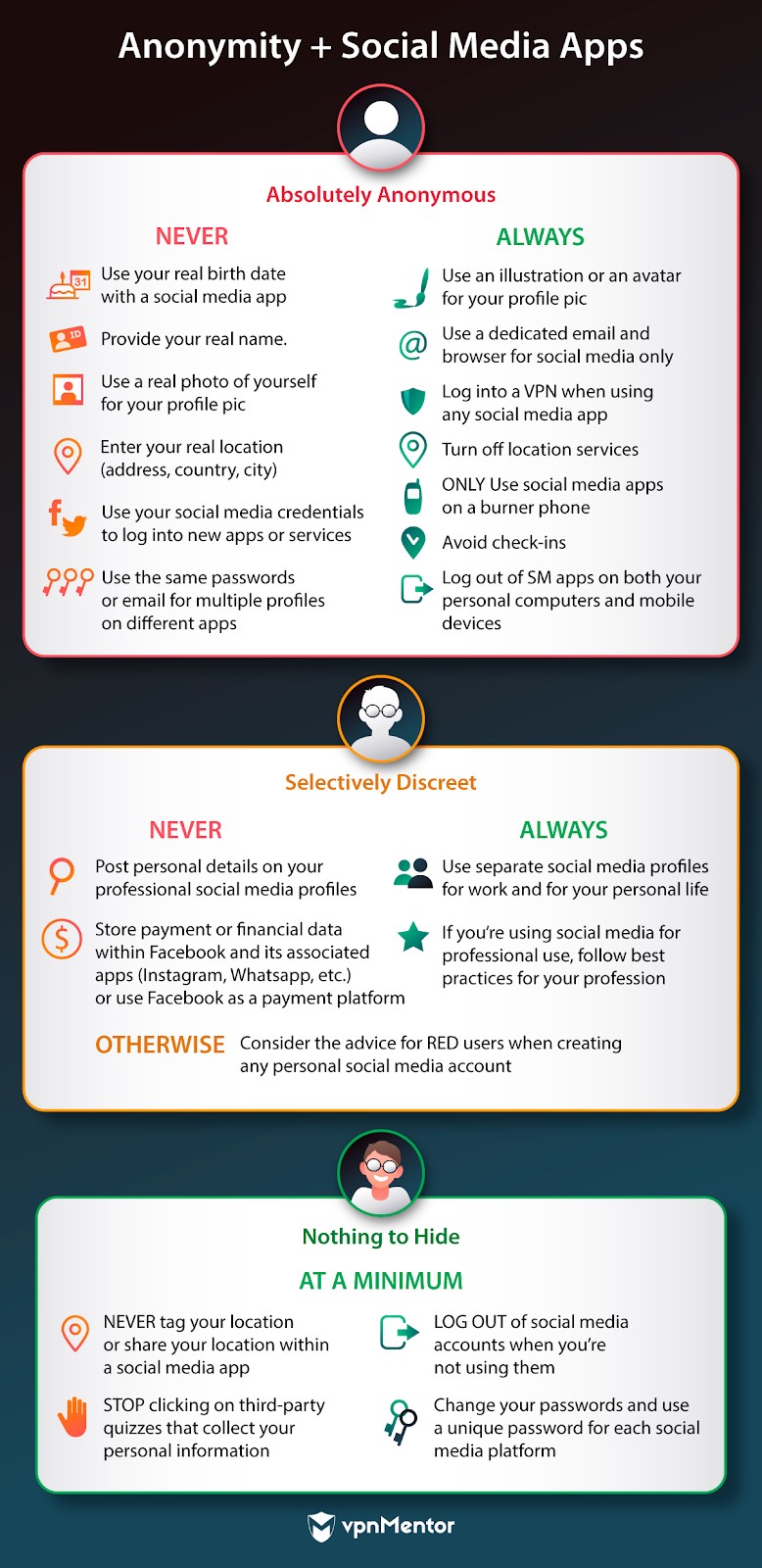
Below is a how-to for using online email while ensuring that your true identity never surfaces.
The session itself (especially if youre using a VPN) is relatively private and inherently secure.
The system in which your information is stored, however?
That anonymity is seriously jeopardized if your personal details (like your account login) is leaked.
Digital marketing and communication professionals often must have personal social media accounts to do their jobs.
While that may have been well-intentioned, people remained unabashedly cruel and often dangerous on both Twitter and Facebook.
Abuse on social media soon became the norm.
So, if verifying your identity wasnt going to stop abuse, why still insist on identity verification?
Post-2016, Facebook now claims its to stop the spread of fake news.

allowed some 100 app developers received access to millions of personal data points.
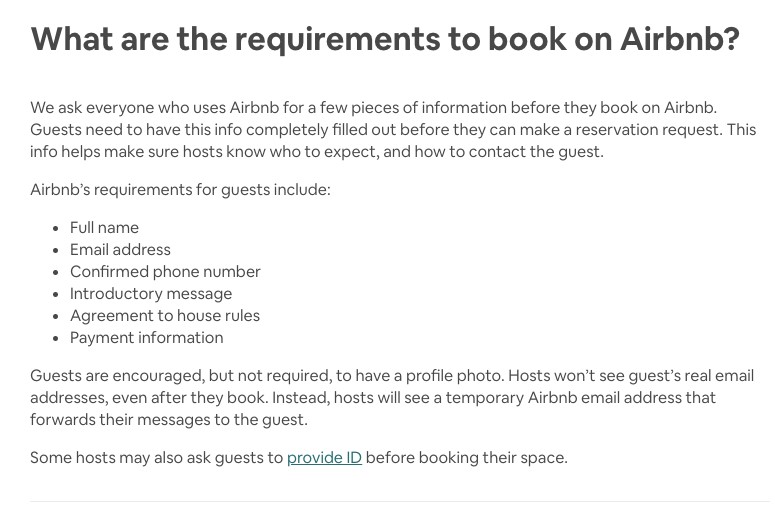
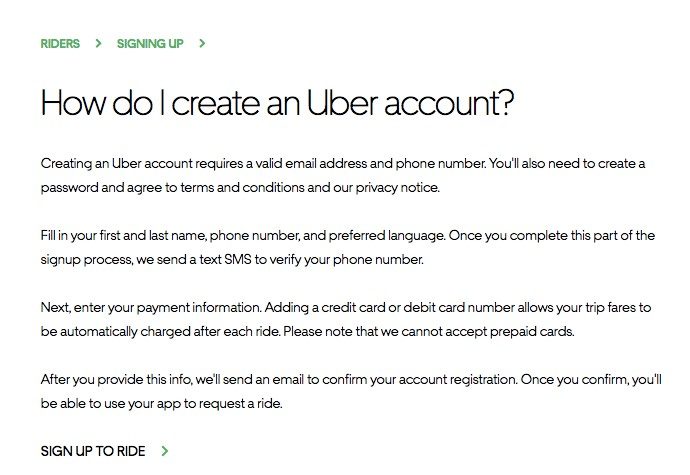
When youre using rideshare and rental apps, its definitely a user-beware situation as bothUberandAirbnbhave suffered massive data breaches.
Always weigh the value and convenience of the service before you decide to become a regular user.
Its a given that using the occasional rideshare may be more affordable than owning your own car.
Airbnb is no stranger to data breaches.
You cant make a reservation request without filling out a basic Airbnb tool.
Uber asks for even less information than Airbnb.
For example, you dont have to secure your home or your work address on the app itself.
The apps location services will find you when you need a ride.
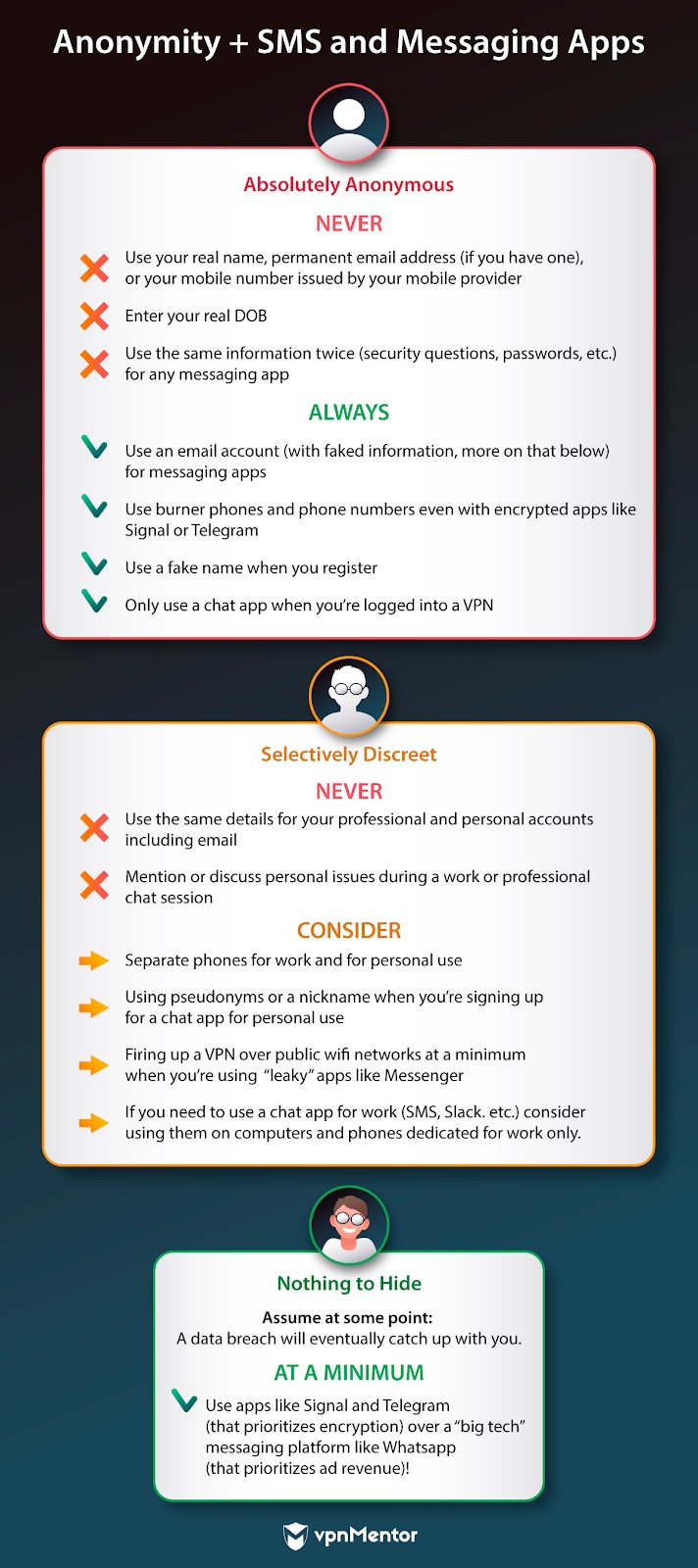
The trick is: how do you do it anonymously?
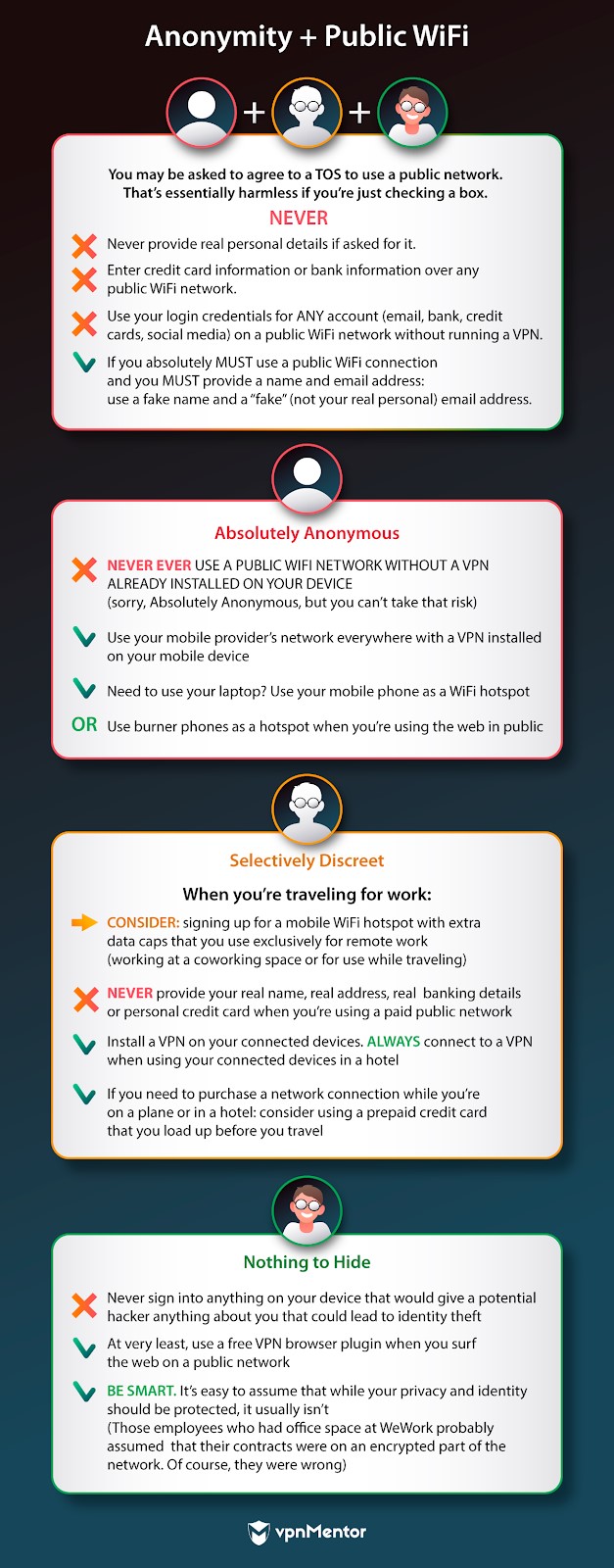
Your online security is tantamount to swiss cheese when youre using a public/free WiFi connection.
The same can also be said for using private networks.
How many other people have the key to that data pipe?
What if a neighbor is able to jump onto their signal at any time?
We all periodically need to take advantage of an open WiFi connection.
Shared coworking spaces and cafes are increasingly popular for busy professionals.
That WiFi in the hotel or cafe is there for a reason: people need it.
As recently as 2019, CNET reported about the massive co-working companyWeWorks baffling wifi vulnerabilities.
Protecting yourself on a public wifi connection is not just good common sense: its your responsibility.
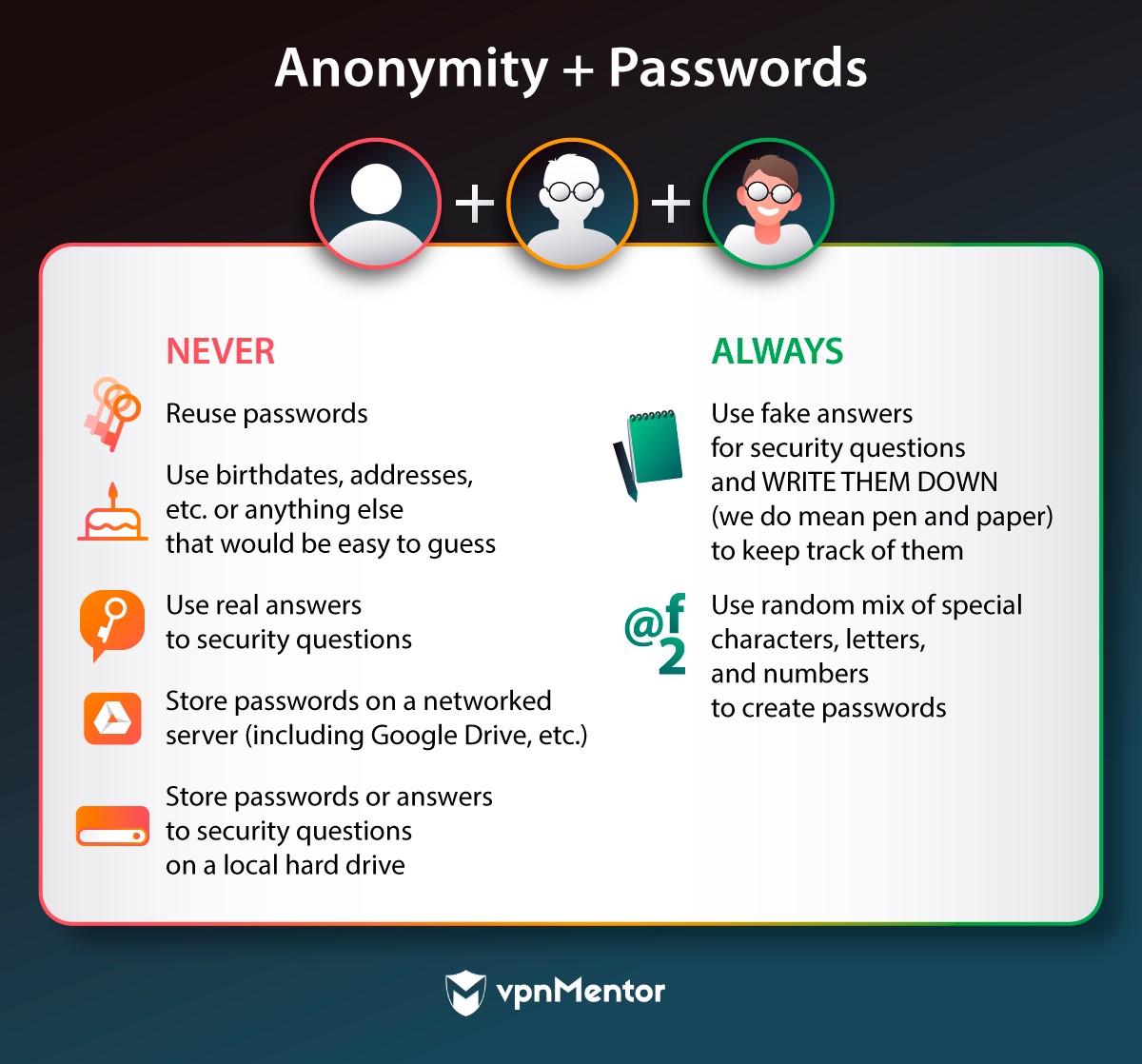
In general: people rarely realize how much information theyre giving away when they create passwords.
Its natural to use personal details because that makes our passwords memorable.

Its less important that your passwords are memorable, and more important that they are anonymized.
PRO TIP:Use vpnMentors password checkerto verify if your password is appropriately strong.
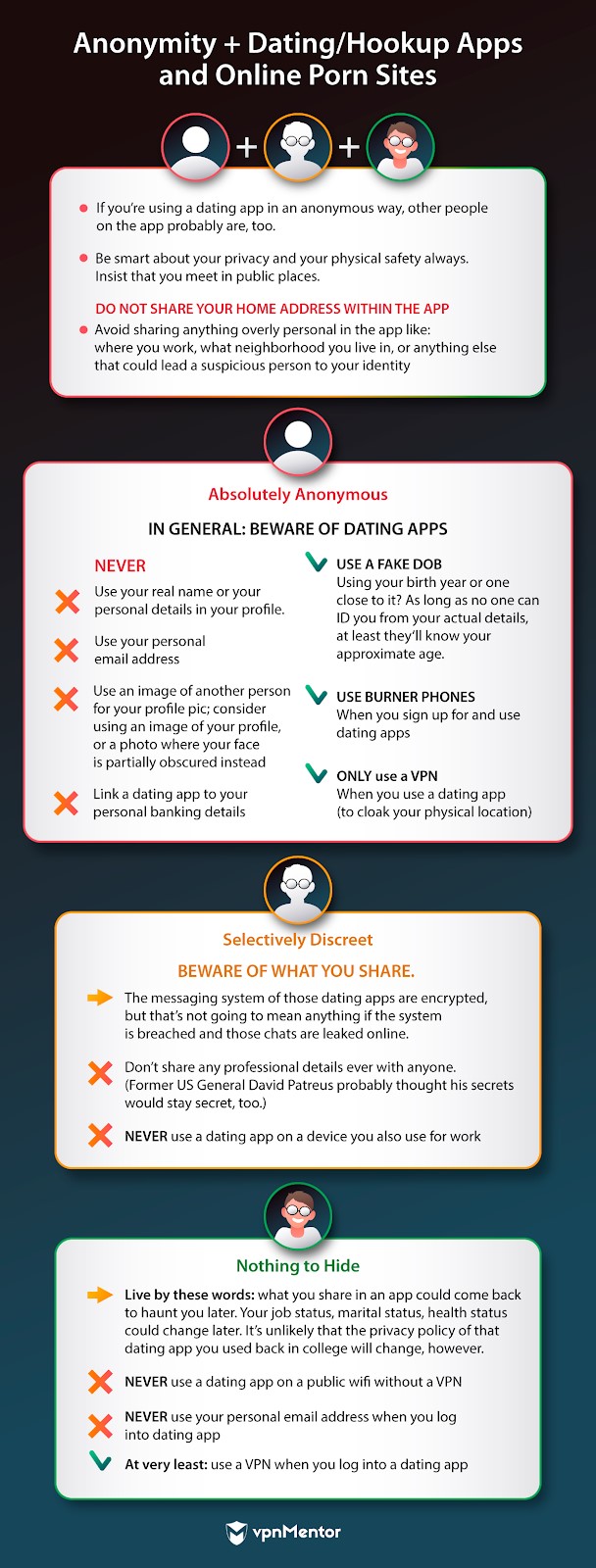
From a security standpoint, those platforms are not merely irresponsible when it comes to protecting your identity.
In 2018,Buzzfeed verified Grindrwas sharing users HIV status and location information with two outside organizations.
Now several years on, users are still livingunder the threat of potential extortion.
This circles us back to the value and utility of an app.
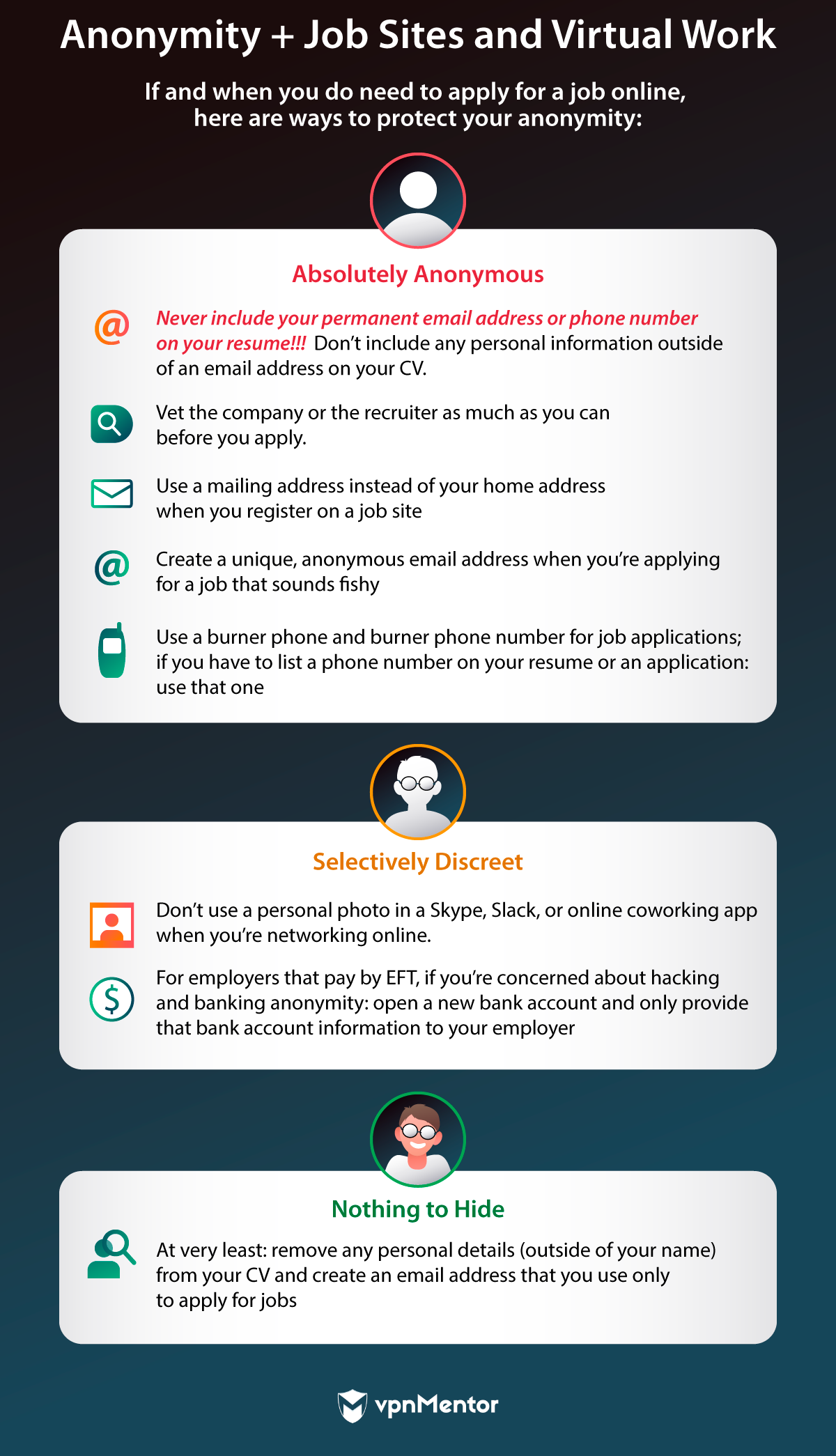
Anonymity + Job Sites and Virtual Work
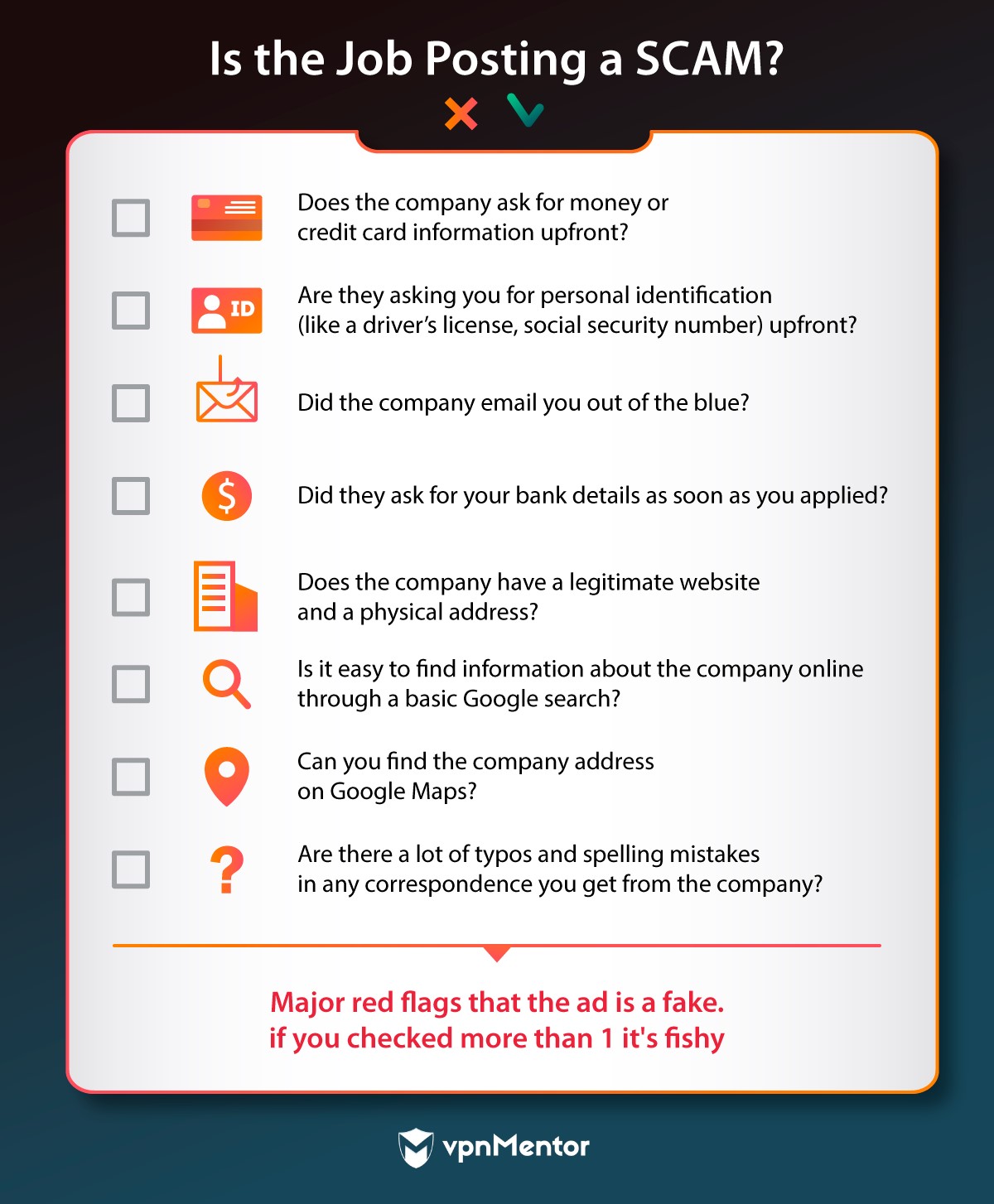
Some general security notes about applying for a job online.
So, before you even apply, give yourself a few minutes to determine if the job is legit.
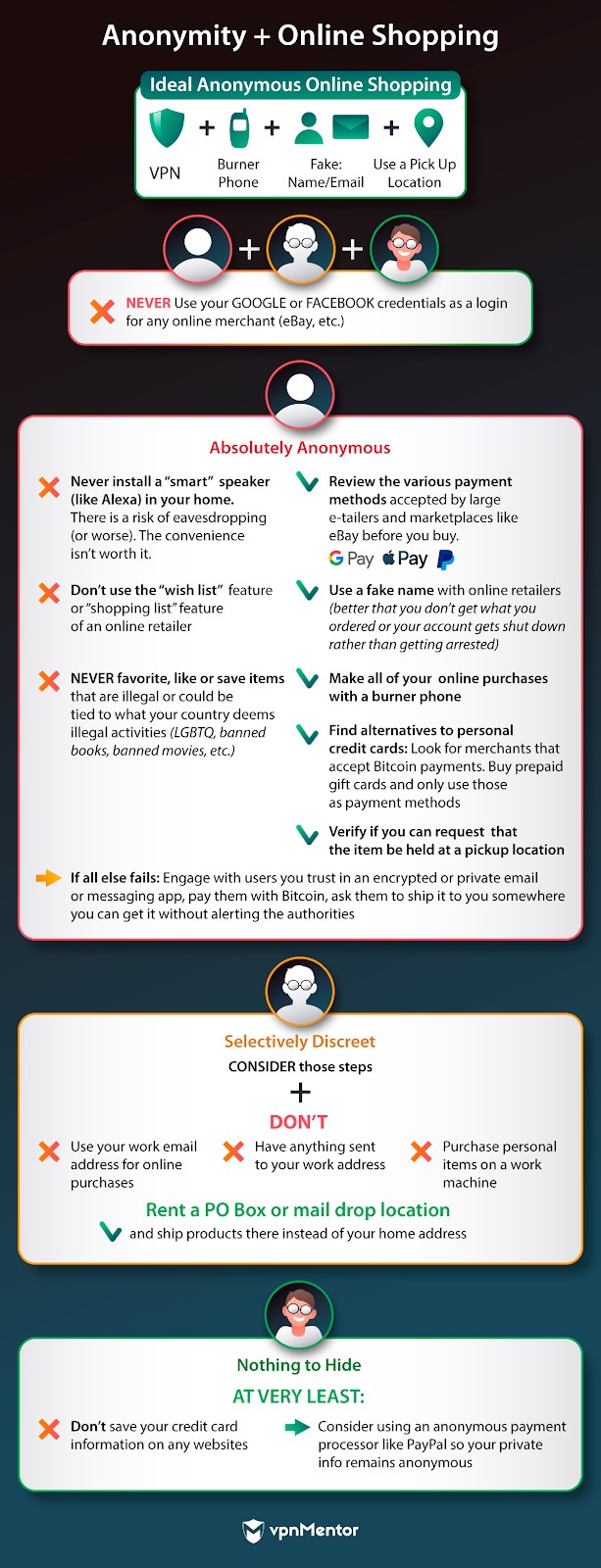
Anonymity + Online Shopping
By 2023,22% of all global retail sales will happen online.
Online shopping is certainly convenient and relatively easy to do from almost any rig you own.
Online retailers, after all,often know a lot about you.
Then, theres also the potential of data breaches.The retail industryis certainly no stranger to them.
The steps below should help keep your identity under wraps as you shop.
Remember, also, that sometimes the convenience isnt worth it.
Anonymity + Online Gaming
Without stating the obvious:people love playing games.
Its increasingly the worlds favorite online pastime.
On the surface, video games are a harmless and fun hobby and a great way to socialize.
Gaming companies understandably focus on more your gaming experience and less your personal security.

The gaming companies are great at a lot of things.
They work with remarkable designers, they certainly deliver engaging and fun content.
Were not saying dont play games.

Instead, beware of how rampant data breaches with even the largest gaming companies can be.
Its evolved into something far more sinister and dangerous, where fellow gamers report fake crimes on other players.
His life was saved when one of the armed officers happened to recognize him from the neighborhood.

The bottom line: paranoia is never a substitution for action and information.


























