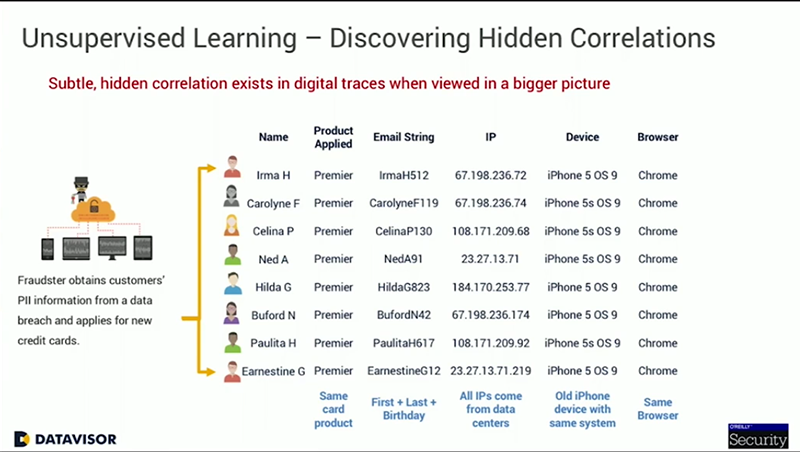
Trying to detect these abusive accounts individually before they can do any damage is nearly impossible.
What are the most significant threats companies and their customers/client/users face from these fraudulent accounts?
In the social sector, we see fraudulent accounts being used to send spam and perpetrate phishing attacks.
can drive a companys stock up or down.
There are also fraudulent purchases made with stolen credit cards, particularly for digital goods such as iTunes.
What are sleeper cells?
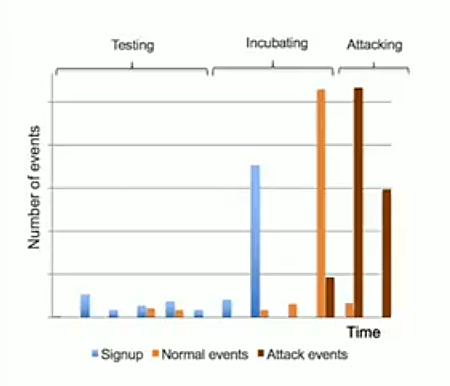
Sleeper cells are becoming more common and are an effective way to avoid detection.
This engagement makes them look like legitimate, active users.
What is gadget flashing and how do bad actors use it to create fraudulent accounts?

This way they get around the detection mechanisms that rely on machine fingerprinting to avoid fraudulent activity.
Indeed, you pose an intriguing inquiry.
However, the reality is that they are all orchestrated from one central point.

This way we have the opportunity to detect these threats.
Secondly, we are looking at these accounts in more than one dimension of the user activity.
When we look at only one dimension, it is a lot easier to be fooled.

They are going to exploit large, and for that, they need many accounts.
In this way, we cast a very wide net to discover those patterns automatically.
What happens once DataVisor identifies an account as fraudulent?
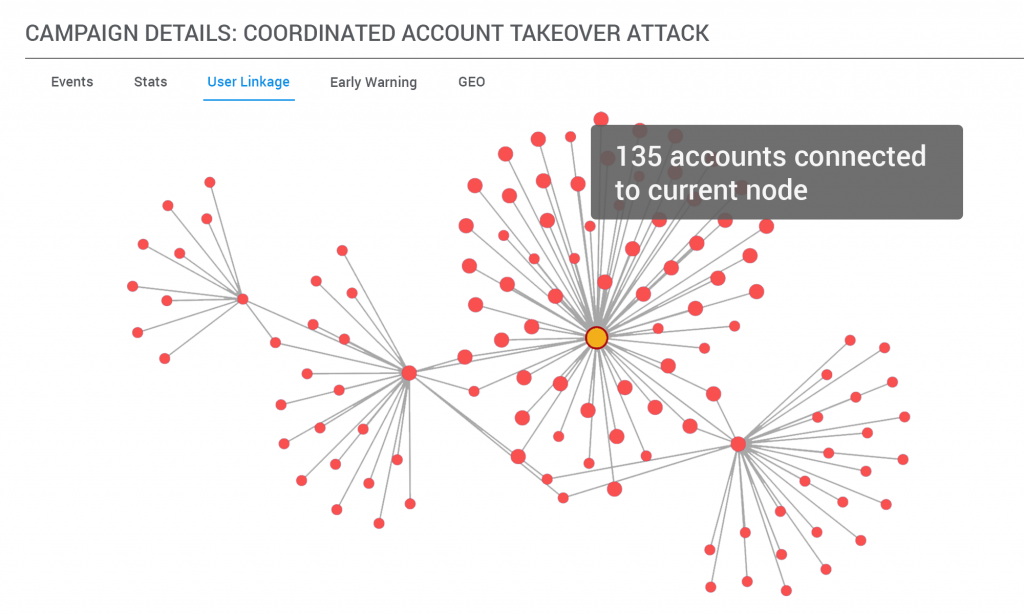
There are many ways to deal with accounts that labeled as suspicious.
For example, a social media service could completely block accounts identified as high confidence ones right away.
In other cases, the service may take steps to validate these accounts further.
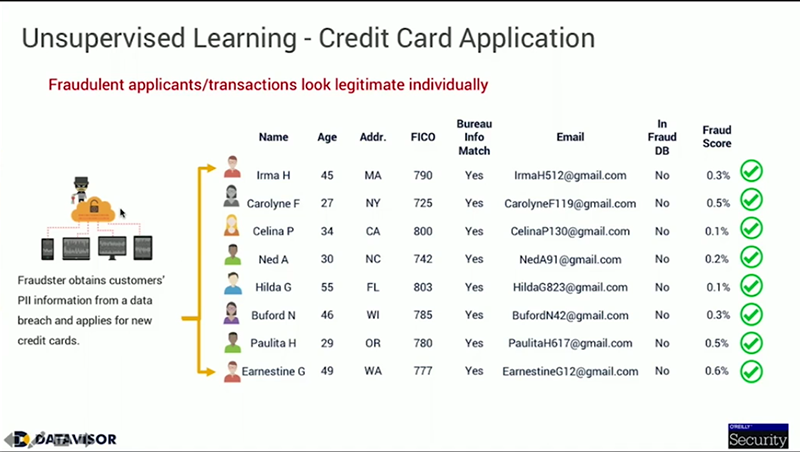
yo, comment on how to improve this article.