Apple devices have featured end-to-end encryption by default for years, using your passcode as the key.
This encryption means that unauthorized access or theft of your devices can’t lead to data or identity theft.
When Are These Features Available?
What Is Contact Key Verification?
What Are Security Keys For Apple ID?
As you don’t need to input any codes yourself, phishing scams are rendered useless.
Image credits:YubiKey 5 Series
Hardware two-step authentication is the most secure method of authentication.
If you do, you may want tolearn the best ways to avoid phishing scamsto keep yourself protected.
Security keys are a more secure alternative to the default two-factor authentication and SMS authentication.
There are some cons, however.
We’ve coveredthe best security keys for online protectionif you are interested in using hardware authentication.
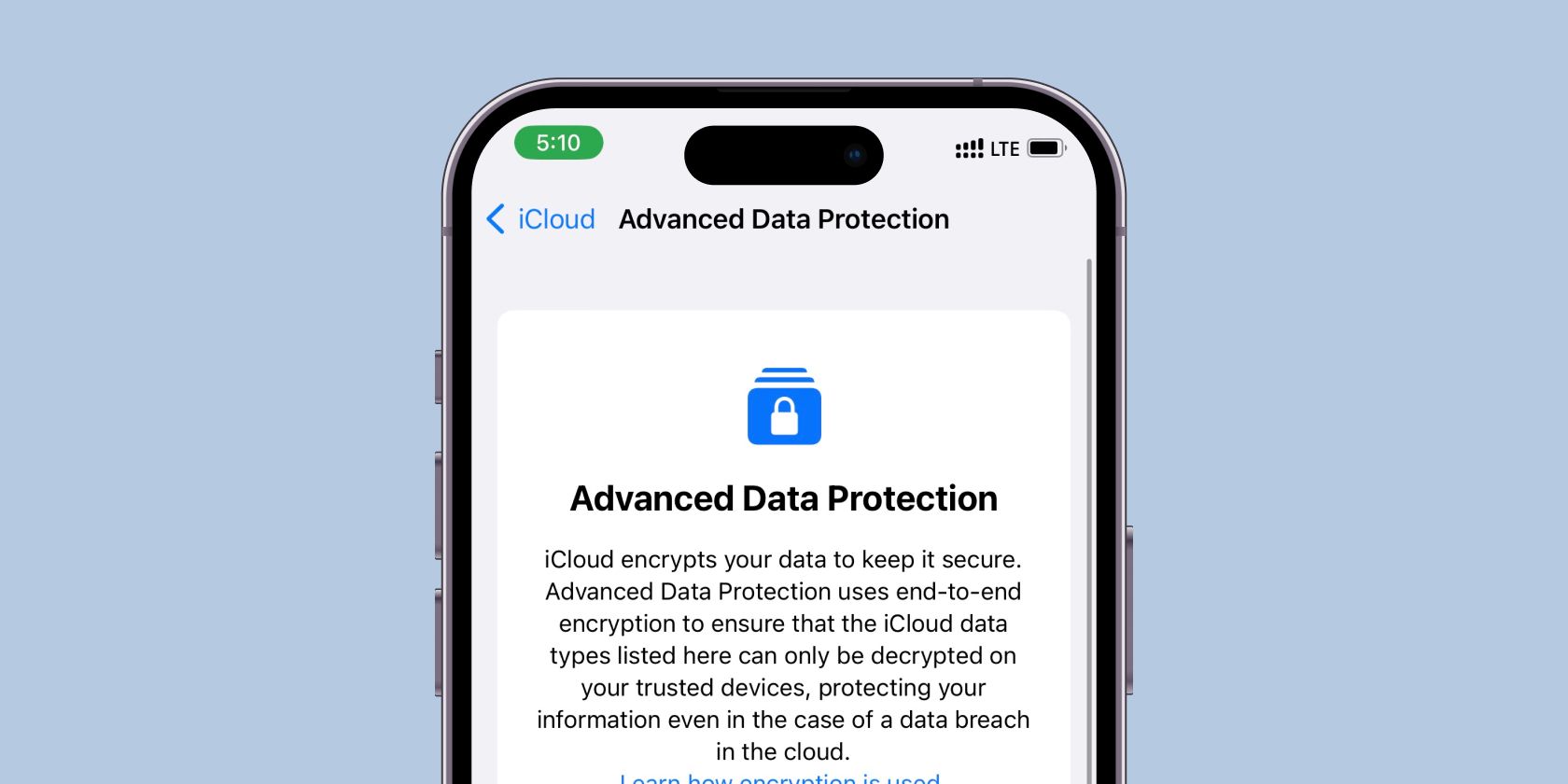
What Is Advanced Data Protection?
Arguably the most important feature introduced by Apple was Advanced Data Protection.
However, only specific types of data are end-to-end encrypted in iCloud on Apple’s servers.
This is why they can be leaked, and the encrypted data can be decrypted by an attacker.
you might explore this in further detail in theiCloud data security overview.
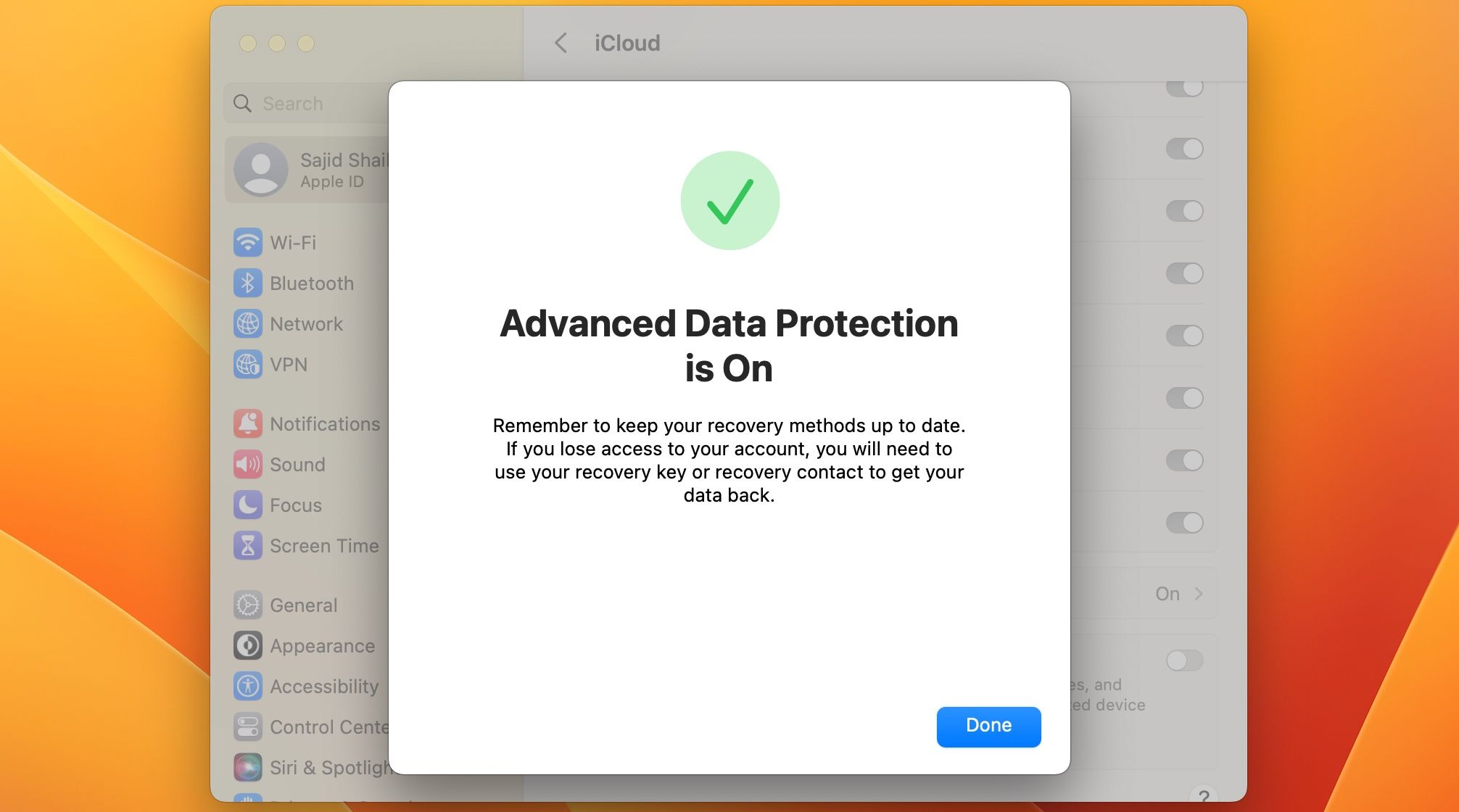
Like Security Keys for Apple ID, Advanced Data Protection does have its own set of cons.
Apple cannot help you recover this data.
We explainhow to enable Advanced Data Protection step by stepand a worldwide rollout is expected in early 2023.
Who Should Use These Features?
Great for avoiding data loss, but detrimental if involved in a breach.
We say if you’re able to guarantee those three things, it might be worth considering.
Will My Account Be Safe Without These Features?
Apple doesn’t recommend these features for average users.
