Protecting your privacy doesn’t have to be complicated.
Maybe your social media account was hacked.
Maybe you’re sick of those disturbingly specific online ads following you wherever you go.

Maybe you just decided to finally face the fact thatyour online privacy may be at risk.
Whatever your reason,protecting your privacy online can seem like an overwhelming task.
The good news is that protecting your privacydoesnt have to be complicated.
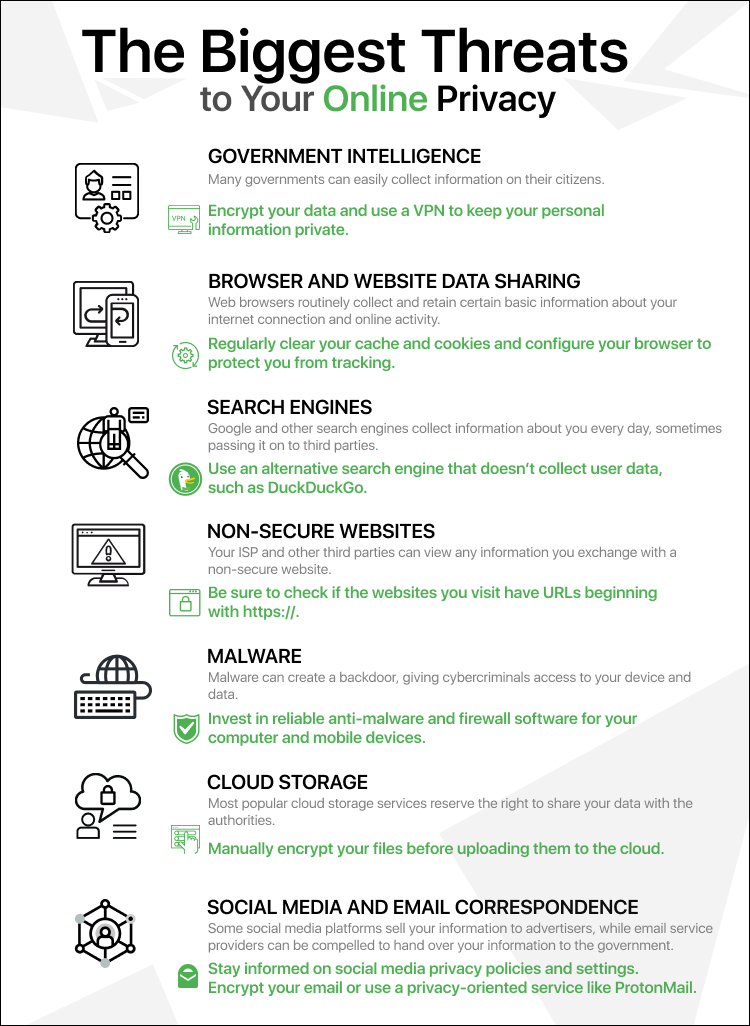
An infographic with information on the biggest threats to online privacy.
What Are the Biggest Threats to Your Online Privacy and Data Security?
We now have a better understanding of how easily many government bodies can gather information on their citizens.
Data that passes through one of the countries in the 14-Eyes Alliance canno longer be assumed to be private.

An infographic with information on the biggest threats to online privacy.
How Does Data Encryption Protect Your Online Privacy?
At its most basic level,encryption is a math equation combined with a secret password or key.
For example, imagine that you send the number 2387 to your friend.

You tell him that all you did was multiply two numbers together to get 2387.
In this scenario, your friend is missing the key you used with your cipher.
But what if you and your friend agreed that in this equation, Y = 7?
Does Encryption Protect Your Data from Government Surveillance?
Modern encryption methods will keep your data secure even from government bodies.
However,encrypted data can attract government attention that may be unwanted.
One downside of encryption is that it stands out to government intelligence organizations.
According to leaked NSA documents, most data collected is deleted after a maximum of five years.
This applies to both foreign and domestic data.
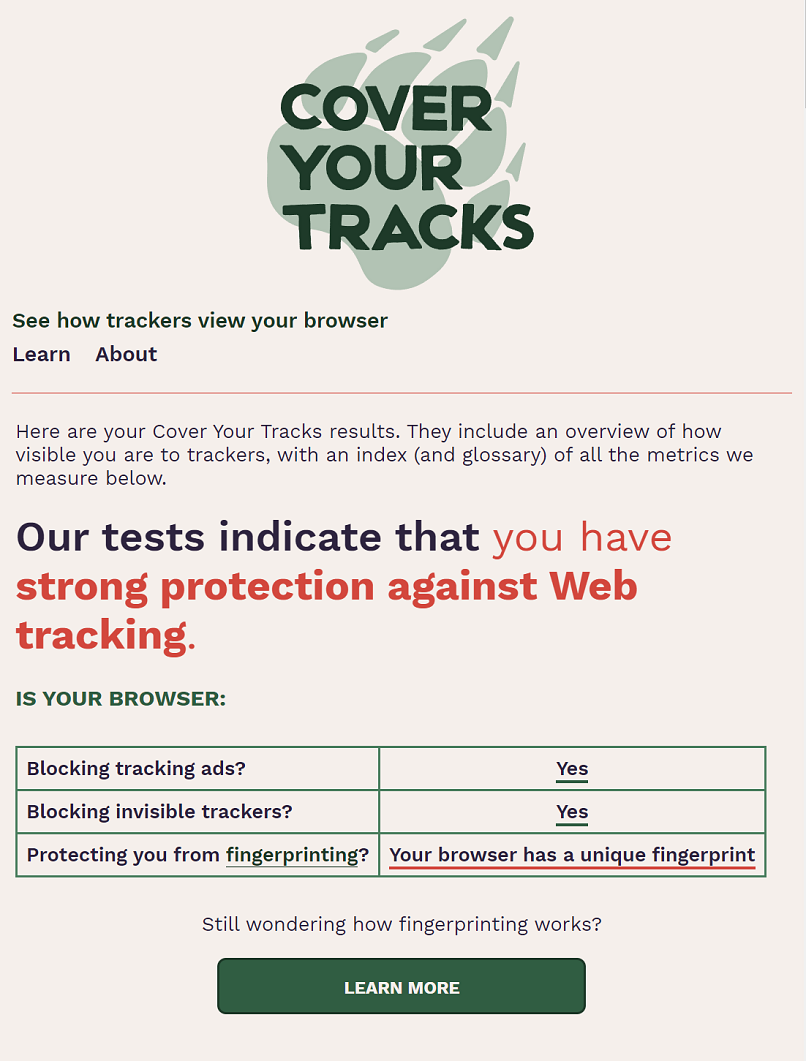
internet tool Fingerprinting
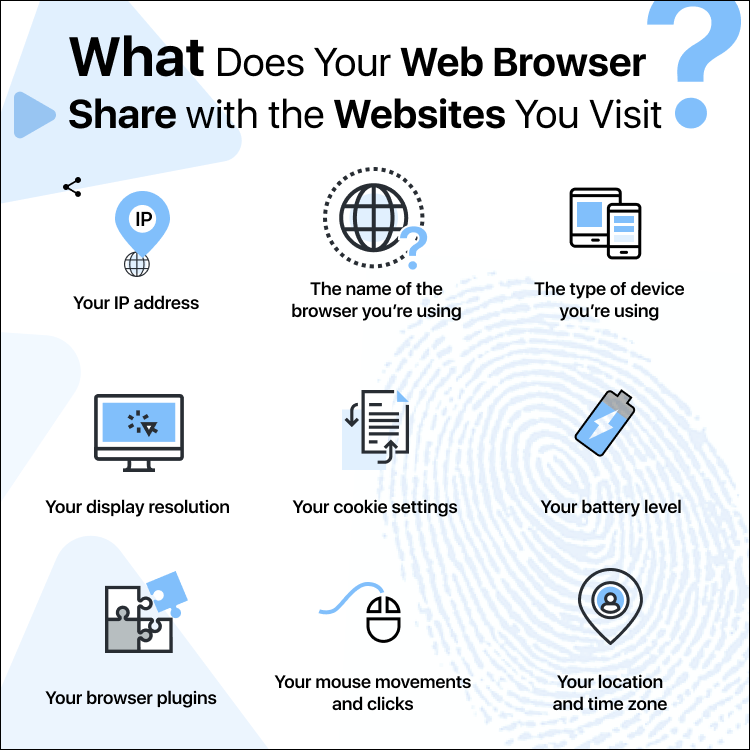
Your mobile internet tool may be handing out much more information than you think.
Third-party analytics can eventrack your online activity across different websites.
One positive use for internet tool fingerprinting is identity theft and fraud prevention.
On the other hand,advertisers love to take advantage of surfing app fingerprinting.
Cookies are small files that websites store on your machine.
The purpose of cookies is to create a customized browsing experience and decrease loading times.
Security-conscious users should be aware of two unique kinds of cookies:Flash cookiesandHTML5 web storage.
Similar to regular HTTP cookies, Flash cookies are small files stored on devices that use Flash.
They contain information about your experience with the Flash elements on the website, impacting your data privacy.
This meansthey arent deleted automatically when you clear your cookies.
Instead, they must be deleted using your Adobe Flash player prefs.
ETags are a kind of HTTP header.
Think about what this means for you.
How often have you searched for something out of curiosity without thinking about possible ramifications?
However,there have been real cases where search histories have been used in legal situations.
In a 2023 arson case, the Colorado Supreme Court issued akeyword search warrantto help identify suspects.
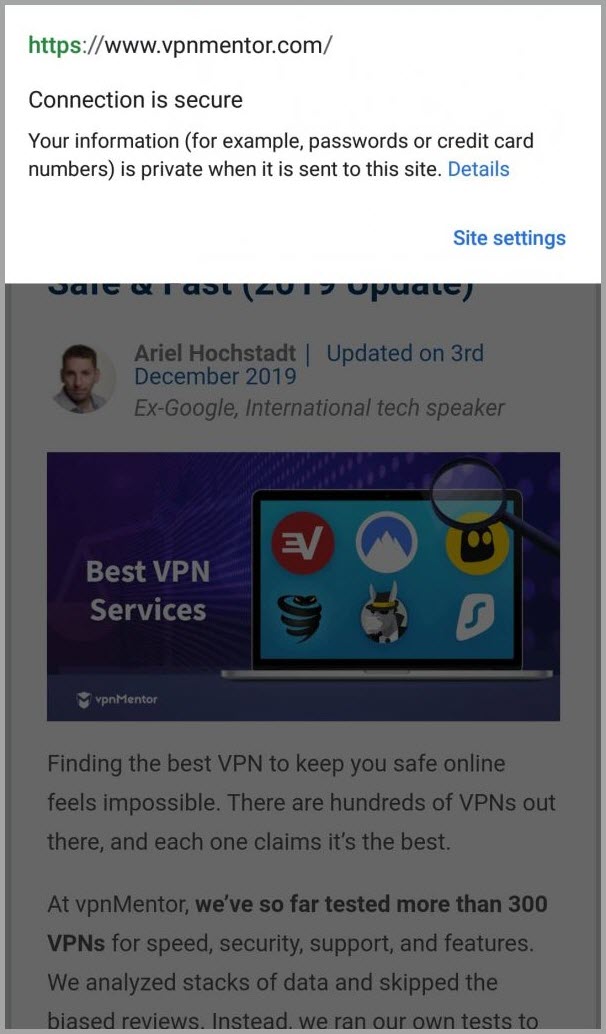
HTTPS stands forHTTP Secureand is also known as HTTP over TLS (Transport Layer Security).
Many web browsers will also notify you if you are visiting a non-secure server.
Protecting your online privacy is crucial in these situations to avoid potential data breaches and identity theft.
Many types of malware can harm your Android equipment or steal your info.
Viruses, worms,ransomware, adware, and spyware are some of the most common.
This kind of software is sometimes known as grayware, and it poses a serious risk to digital privacy.
Since the company encrypts your data, it also holds the key to unencrypting it.
Many of them have also been known to cooperate with the NSA.

If the NSA has the ability to access it,your data is no longer truly private.
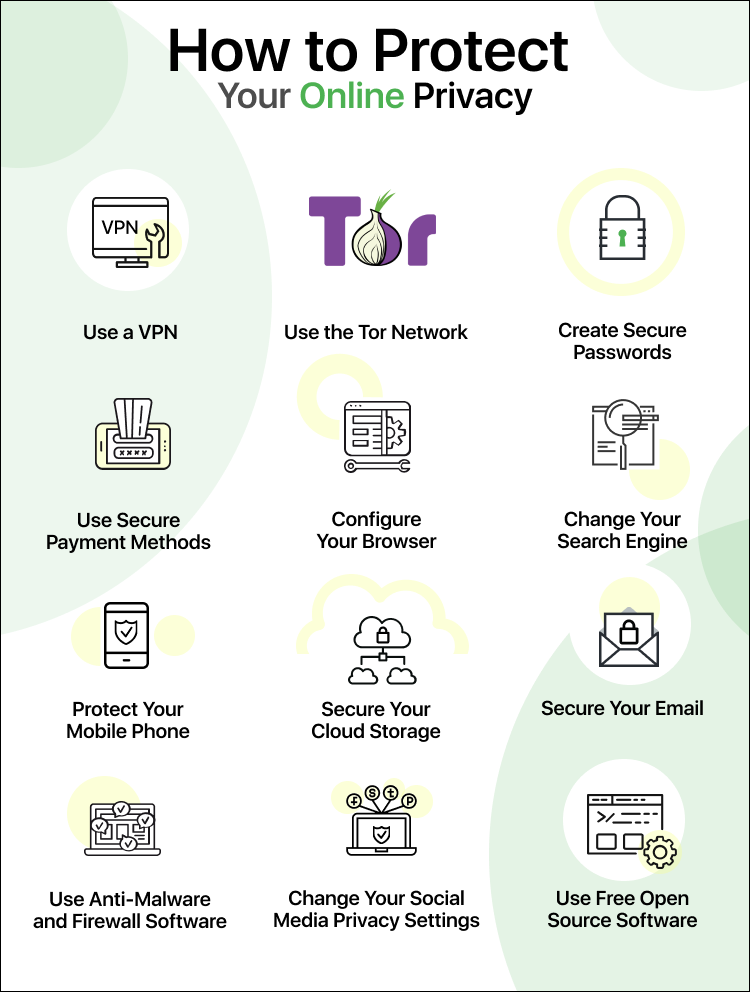
What Steps Can You Take to Protect Your Online Privacy?
Including these devices in our privacy protection efforts is now more important than ever.
You might be feeling overwhelmed after reading about some ofthe biggest threats to your online privacy.
Take a deep breath.
After acomprehensive review, I recommendExpressVPNas my top choice for online privacy protection.
A VPN, on the other hand, will protect your internet connectionto stop privacy breaches before they happen.
Preventing a security problem is much easier than fixing one.
Here are a few of the major privacy protection features that most VPN services offer.
Encryption
There are two main pieces to consider when it comes to encryption strength.
The second piece to consider is theencryption key length.
This is calledbrute force.
An 8-bit encryption key has only 256 possible combinations, so brute force is likely to be successful.
Now consider how many combinations are possible with a 128-bit key and then further with a 256-bit key.
OpenVPN
OpenVPN is open-source software that offersa secure protocolused by many VPN providers.
OpenVPN essentially routes your VPN connection through the secure channels it creates toprotect you from data leaks.
It provides a very secure layer of privacy protection.
With a typical encryption tool, your data is secured using a single encryption key.
If that key were to be compromised, your data would no longer be secure.
The rest of your data would remain secure.
This is because the VPN provider could be compelled to hand over your information to authorities.
Compared to a VPN, using the Tor web connection has both advantages and disadvantages.
To connect to Tor on Android, it’s crucial that you use itsOrbot package.
vpnMentoroffers a digital privacy toolto help you generate highly secure passwords.

A recent federal ruling says the act is unconstitutional, but there’s a possibility it may be overruled.
Legalities aside, fingerprint technology can be faulty.
Reports have surfaced of some Samsung Galaxy devices allowing any fingerprint to unlock a gadget.

If you’re using a computer, you’re able to also find them as internet tool extensions.
Many mobile browsers, including Chrome and Firefox, offer built-in password managers.
For now, sticking with a secure third-party password manager may be best.

Some banks offer extra levels of security for online shopping.
Citi givesvirtual account numberstodisguise users' real data, also helping protect their data online.
France’s Societe Generale takes cryptosecurity one step further byoffering users CVV numbers that update periodically.

PayPal is another option for protecting online payment.
They even have aBug Bounty Programthat offers financial rewards to anyone who can discover and report any site vulnerabilities.
Regularly clearing your DNS cache and cookiescan limit your risk of being fingerprinted and tracked through your online window.

Look for a guide online for your specific web client and Android machine.
Many browsers also have options that allow you to limit the cookies that you accept.
Taking time toproperly review and configure your browsercan do a lot to protect you from tracking.

Using the Tor networkis one effective way to lower your risk of surfing app fingerprinting.
One of the most popular search engines for PCs and Android that doesnt collect user data isDuckDuckGo.
This doesnt mean you have to give up on cloud storage altogether, though.

Your cloud storage provider will have no way to access your data.
How to Protect Your Privacy Online through Data Encryption
Wondering how you could encrypt your data manually?
I’m going to walk you through the steps.

By manually encrypting your files, you could ensure that your cloud storage service cant access your data.
This example will walk you through how to encrypt your data using the mobile app Boxcryptor.
You canchoose any software that meets the following criteria:
That last point is very important.

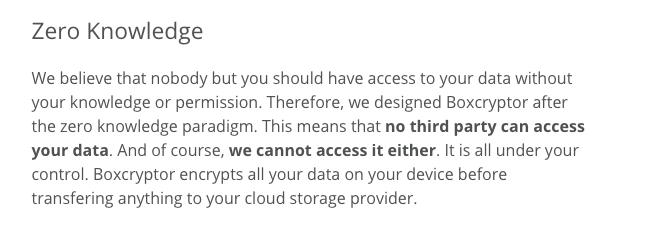
Look for a statement like this one from Boxcryptor:
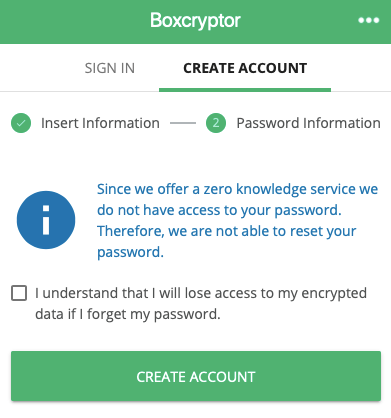
2.
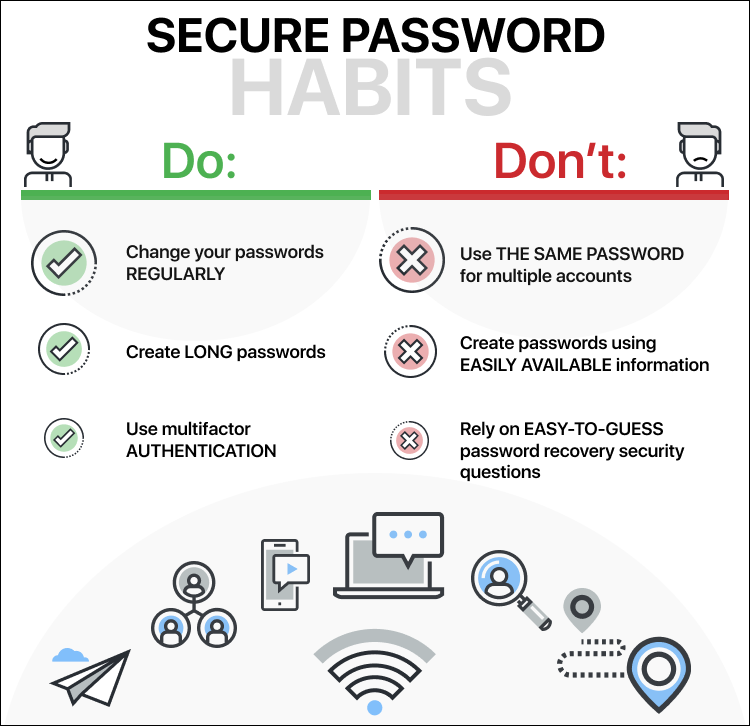
Create a secure passwordand dont forget it!
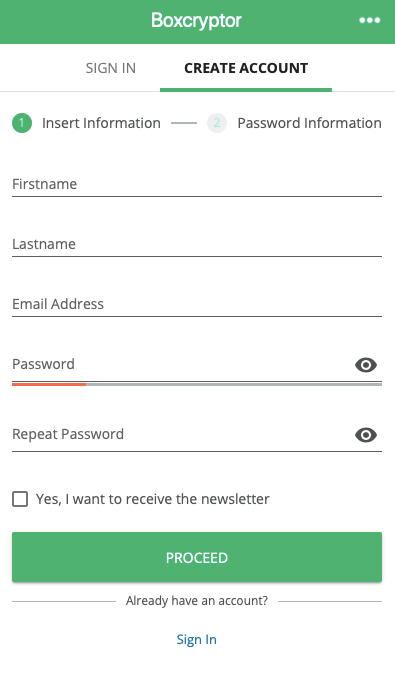
When you first open Boxcryptor, it prompts you to create an account.

As part of this process, you’ll be asked to choose a password.
This is extremely important.
The password you choose is your key to encrypting and decrypting your data.

It should be unique, private, and secure.
You also need to take steps to ensure you’ll never forget your password.
This could lead to you losing access to your own data.

Add a cloud provider
Boxcryptor will ask you to set up a cloud service provider.
After you’ve connected to a provider, Boxcryptor lets you access your files and folders.
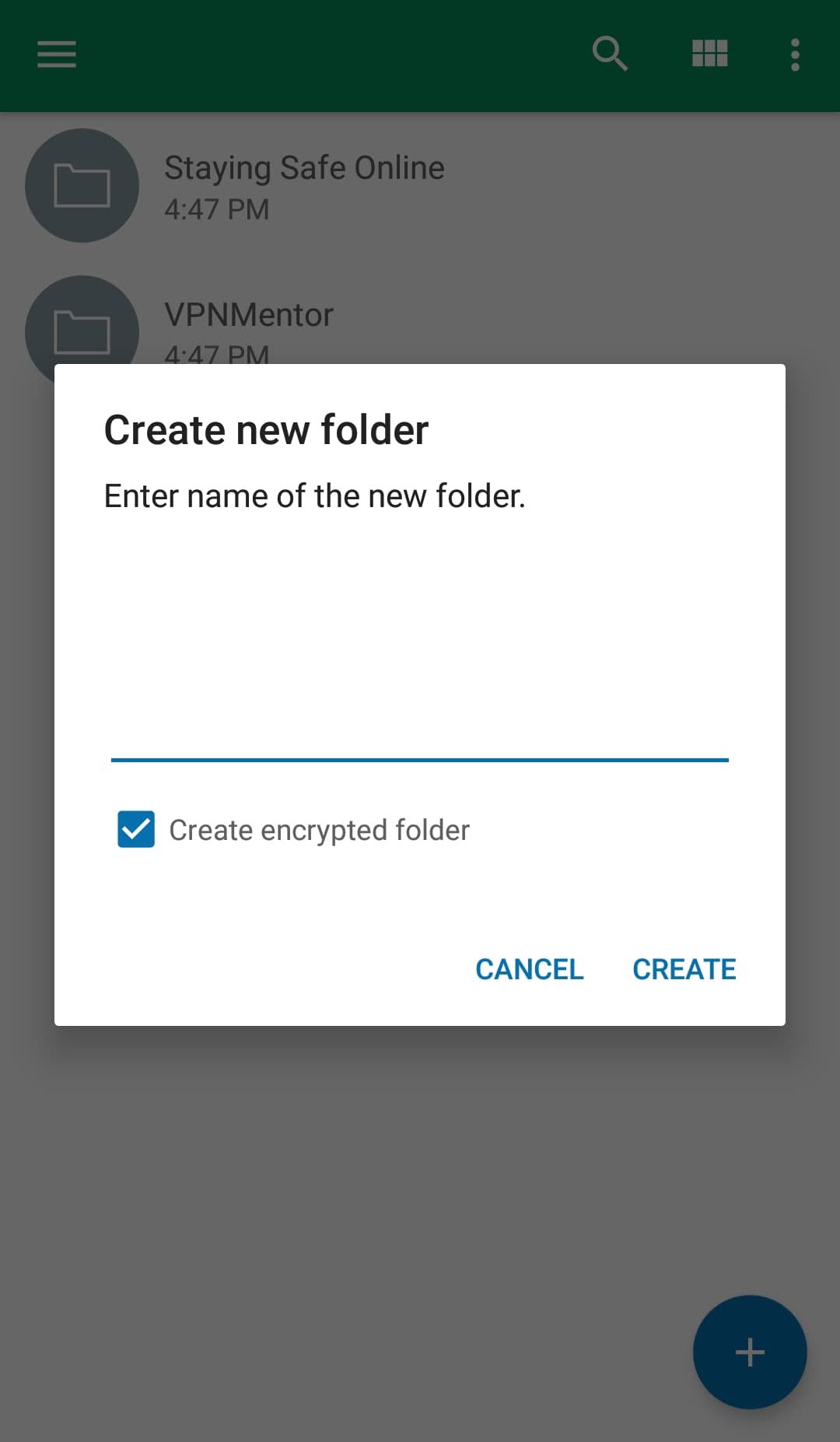
You’ll see the following message:
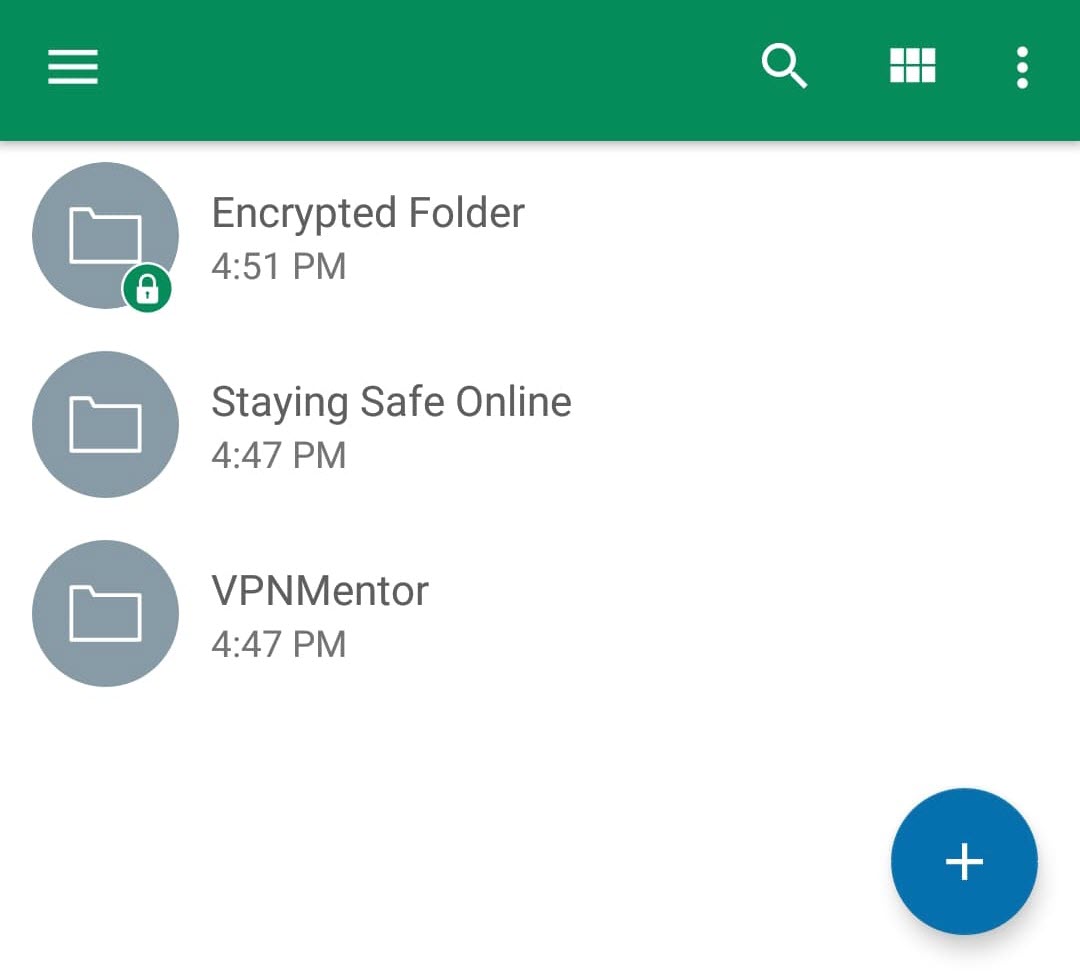
Enter a file name and click “create” to proceed.

Your encrypted folder is denoted with a green lock.
Now, any file you add to this folder is automatically encrypted and uploaded to your cloud storage.
Major email services put a lot of effort into creatingrobust security measuresand quickly fixing vulnerabilities.

The problem is thatmost methods of encrypting your email are far from practical.
After all,you need your recipient to decrypt your message to make it read it.
They monitor app actions to ensure that no unauthorized data is being downloaded or sent by your rig.
This can make it impossible for invasive malware to share your private information, strengthening your privacy protection.
This data could even be used to threaten or harm you.
The first is tospend some time reading and researching the privacy policies of the companies that control your accounts.
The second thing you should do ismonitor your privacy controls.
Check these options regularly to see to it that nothing has changed as the platform updates.
VPNs for Android devices make it easy to personalize your protection and address your biggest privacy concerns directly.
kindly, comment on how to improve this article.
