TheSafetyDetectivescybersecurity team uncovered an open ElasticSearch database exposing an organized fake reviews scam affecting Amazon.
These Amazon vendors send to reviewers a list of items/products for which they would like a 5-star review.
The refund for any purchased goods is actioned through PayPal and not directly through Amazons platform.
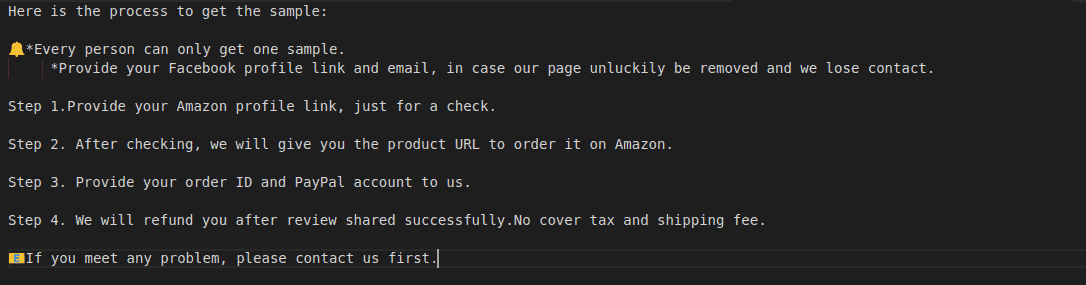
Amazon vendors paying for reviews
This makes the five-star review look legitimate, so as not to arouse suspicion from Amazon moderators.
However, we didnt find any examples of this in the exposed server.
What was Leaked?
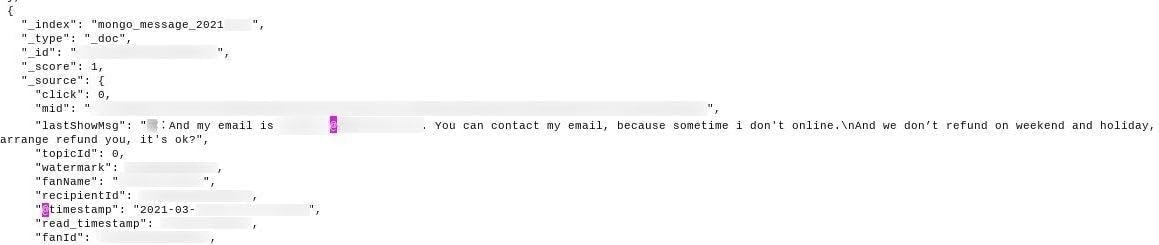
Contact details of vendors, such as email addresses
Contact details of vendors, such as email addresses
2.
These details could be used to indirectly identify individuals, while many of them contained full names and surnames.
The Gmail addresses of reviewers were also provided to vendors directly via message.
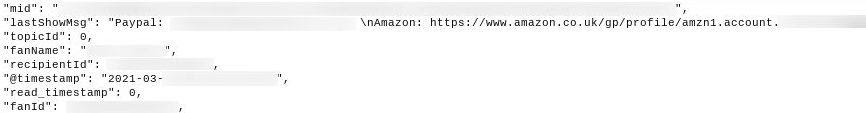
Links to Amazon accounts
75,000 Amazon accounts were leaked as well, although there are potentially several duplicates included in this figure.
In reality, the leak could have affected individuals from all corners of the world.
The SafetyDetectives cybersecurity team discovered the breach on March 1st, 2021.
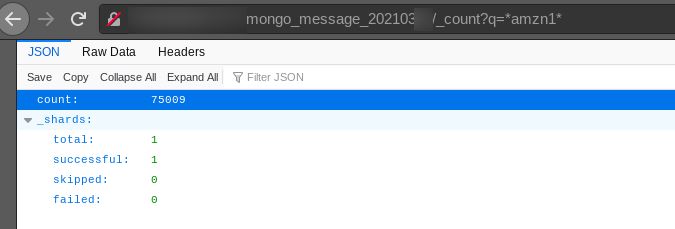
Count of records containing Amazon profile link
We were unable to identify the owner of the ElasticSearch server.
As a result, we could not notify the company in question regarding this security issue.
Nonetheless, the server was secured a few days later, making it inaccessible to outside parties.

PayPal emails of fake reviewers
Implicated vendors can avoid detection across multiple platforms, too.
Messages in the unclaimed ElasticSearch server highlighted techniques that are employed by businesses to cover their tracks.
Fraudulent businesses give reviewers specific criteria to follow to avoid detection on Amazon.

Emails and ‘fan names’ are included in messages
These criteria are designed to present the reviews as legitimate.
In this ElasticSearch server, vendors asked reviewers to wait a few days before publishing a review.
Instructions were sent to reviewers to make the reviews more credible.
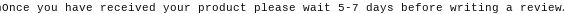
Instructions were sent to reviewers to make the reviews more credible
In the ElasticSearch server we discovered, vendors attempted to hide keywords with similar phrases that bypass keyword searches.
However, this is merely an educated assumption.
This is certainly the case in the database we detected.

Some vendors requested reviews over a specific word count
Impacts
The owners of the ElasticSearch server have essentially committed two separate offenses.
On one hand, companies and individuals have been connected with the production of misleading marketing materials.
We can split these impacts into two different types:Corporate punishmentsandindividual punishments.

Amazon vendors are disguising keywords to evade detection
Firstly, Amazon vendors have broken Amazons terms of service through buying fake reviews.
Amazon can place a number of sanctions on guilty parties.
Vendor accounts can be terminated permanently, and vendors can lose their selling privileges with an immediate effect.
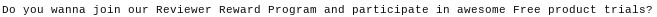
‘Official’ language presents the vendor as a legitimate business
Products can even be delisted from the site altogether.
Amazon retains the right to disclose the vendors name (and any other related information) publicly.
Amazons terms of service outline that Amazon may choose to pursue legal action against the business involved.
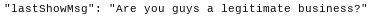
One potential reviewer seems unaware of the consequences
Using deceptive marketing tactics could land a US-based vendor with a heavy penalty of more than $10 million.
The breach also means people exposed as fake review sellers may be subject to lawful punishment themselves.
The severity of these punishments would depend on whichever jurisdiction is in control of the investigation.
The fraudulent owner of the server seems to be based in China.
If individuals from other nations are affected, other jurisdictions could also carry out investigations.
Future customers may choose to avoid businesses involved in lawsuits, unlawful activities, or poor data protection practices.
It is currently unknown whether hackers accessed the open ElasticSearch server.
With something as simple as an email address, a hacker could launch a phishing attack.
Hackers could pose as a representative of PayPal, requesting that users update their password.
Hackers can pepper leaked PayPal accounts with generated passwords until they gain access.
For example, transaction history could be used to pose as a representative of another business.
The obvious risk associated with incriminating data means hackers could target victims with blackmail.
Fake reviews deny potential buyers a fair and honest assessment of products at the benefit of the vendor involved.
Buyers may ultimately be underwhelmed with the product, or feel deceived by the reviews they have read.
These bundles can contain up to 1000 reviews for a price of around $11,000.
Spotting and reporting suspected fake reviews helps protect ourselves and other consumers.
Reporting such incidents could provide crucial support to marketplaces trying to contain the problem.
Most online marketplaces have a symbol of a flag or an exclamation mark next to each comment.
On Amazon, there is a report button.
Clicking this will take you through the referral process.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, followSafetyDetectives Cybersecurity Team.
Published on: May 6, 2021