The problem comes in figuring out where to start.
Cybersecurity can feel overwhelming and terribly complicated.
Weve put together this guide just for this punch in of person.

Securing your business is really not as difficult as many experts make it out to be.
If you dont know what your weaknesses are, how will you be able to fix them?
If you dont know what kind of data your company stores, how will you protect it?

Start by identifying the crown jewels of your company data.
What are the most crucial pieces of data that your company holds?
Where do you store all of this data?

Think about all the transit points along the way through which this data could leak out or get stolen.
After doing so, you’re able to start to put precautions in place.
These are our guidelines for boosting your security across the spectrum of your companys computer systems.

Criminal hackers spend their time searching for bugs in popular software, exploiting loopholes to get into the system.
This kind of intrusion can cause untold damage to your business.
Hackers could steal your customers credit card numbers from your website, or steal passwords from your setup.
Your business could be in real trouble if this happens.
Microsoft and other software companies are always on the lookout for vulnerabilities in their software.
When they find one, they release an update for users to download.

Luckily the attack was stopped, but this is not always the case.
The easiest way to avoid becoming the hackers next victim is to conscientiously tune up your software.
Protect against viruses
Viruses are malicious programs that infect your system without any warning.
Viruses spread quickly by replicating and sending themselves to the people in your contacts list.
Malware and ransomware are the two most dangerous types of virus in circulation today.
There are a fewdifferences between malware and ransomware.

Malware stands for malicious software.
It works by tricking the victim into downloading certain software, thereby gaining access to that victims computer.
It can trace what you access on your setup, steal sensitive information, or spread spam via email.
Ransomware is a specific throw in of malware.
It locks your system and blocks you from accessing your important files until you pay the ransom.
Ransomware works by encrypting your files using a private key accessible only to its creators.
The WannaCry attack mentioned above was a pop in of ransomware.
Paying the ransom doesnt necessarily help: there is no guarantee that the hackers will actually unlock your files.
First, install antivirus software on all office computers.
Hackers are always putting out new viruses, so you should patch your antivirus software regularly.
The best software providers will include a feature that commands your box to download the updates automatically.
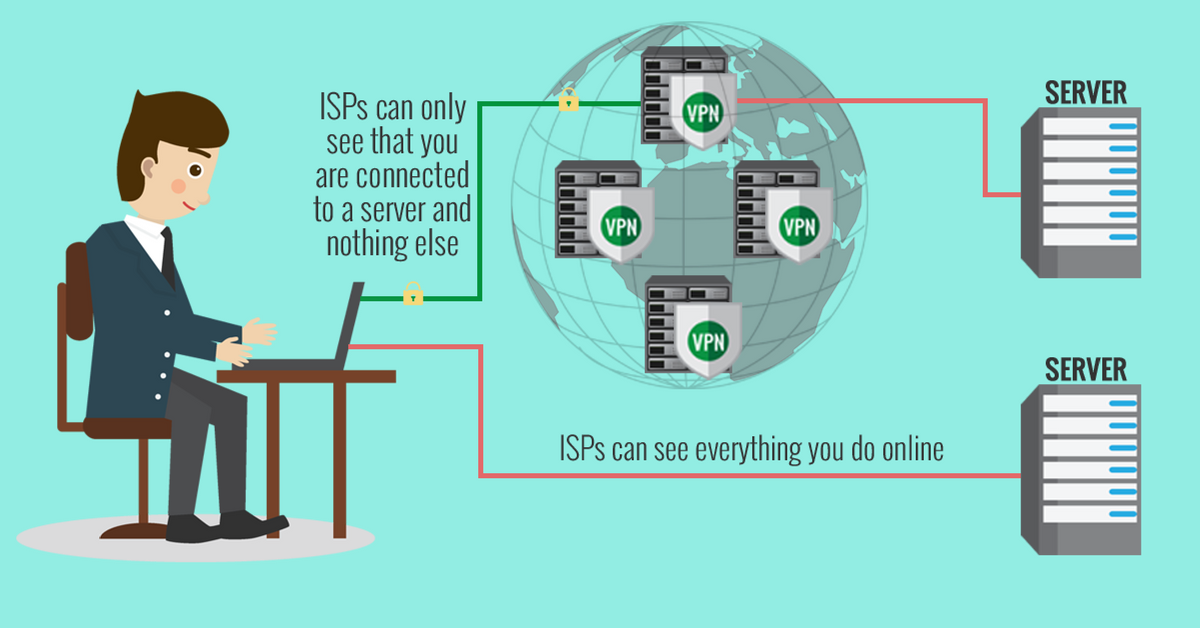
Using a VPN to get into the internet can also give you anextra security boost.
Good VPN providers send you a security warning when you make a run at access suspicious URLs.
If youre already the victim of a ransomware attack, its not too late.
Thisstep-by-step guidewill help you beat an attack.
Installing a firewall is the best way to prevent this kind of attack from happening.
Installing a firewall is complicated and should only be done by a trained professional.
They are a target for thieves because they are easy to steal and then sell.

However, replacing a laptop is a significant financial outlay, especially for a small business.
But this isnt even the biggest problem.
Laptops should be kept in carry-on luggage, and not left in baggage storage areas in hotels or airports.
These guidelines are especially pertinent in regard to laptops.
We explore them further in section 3, Protect your data.
It pays to plan ahead for the eventuality that one of your company devices will get stolen.
The major cloud computing providers allow you to wipe an account from any unit that goes missing.
All of this advice applies equally to company smartphones.
is by installing a VPN to encrypt all of the data moving through these devices.
That way, all of the devices that use the office internet connection will be protected.
Your data can get lost in all manner of ways.
Implement a procedure to back up critical data
There are two different types of backups.
The easiest and most efficient method is to combine the two.
Perform a full backup periodically and an incremental backup every day in between.
Or, you might perform a full backup every night after work hours.
There are many different ways to backup your data.
you’re free to also keep backups at a secure offsite location.
We strongly recommend that all companies invest in a cloud-based backup system see the next section for further details.

There are a number of approaches you might take to double-check your files in the cloud are secure.
Just confirm not to upload your encryption keys.
That being said, you should investigate your cloud storage options carefully.

Some of these services will automatically encrypt your files before they are uploaded to the cloud.
Another option entirely is to use BitTorrent Sync, which is a totally free service.
BitTorrent Sync was designed as a replacement for cloud-based systems but does not actually store files in the cloud.

Instead, it enables you to collaborate on documents through a peer-to-peer (P2P) file-sharing platform.
Thisultimate guide to online privacyexplains it even more.
However, passwords are also open to attack.

Hackers have developed sophisticated, automated tools that enable them to crack simple passwords in just a few minutes.
Passwords can become ineffective for a variety of reasons.
so that avoid forgetting their passwords, many employees write them down in plain sight.

All of these mistakes leave the door open for hackers.
Theseseven steps to creating a strong passwordwill help prevent hack attacks:
Creating a stronger password isnt that difficult.
you’re free to also use asecure random password generatorthat will create a completely randomized password.

Take steps to restrict access to your system.
Companies can also be lax by allowing multiple staff members to share one login and password.
This makes it impossible to determine how or when a breach in your system occurred.

Give each user his or her own account, enabled with permissions specific to his or her job.
Intruders who can gain access to your connection can steal your files and damage your systems.
If youre using a Wi-Fi data pipe, confirm you have these security features switched on.
These activities can then be aggregated by third-party agents without your consent.
Your employees could inadvertently browse to dangerous websites that steal your companys data.
And your personal or business information could be compromised if it is entered into websites over a non-encrypted connection.
A VPN, or virtual private online grid, masks your companys IP address and encrypts your browsing data.
The downside to using a VPN is that trustworthy and feature-rich VPN services cost money for a monthly subscription.
Many individuals and companies have opted to use afree web proxyas an alternative.
With the internet, working with others across the world is easy to do.
However, remote work comes with some cybersecurity pitfalls.
Windows offers a remote desktop connection feature, but this in itself is not enough to secure your data.
H. Protect your customers data
Its one thing if your sensitive company data is lost or stolen.
Its another matter entirely if your clients or customers data is compromised.
Typically, customer data is in transit through multiple points.
This will ensure that your clients data is encrypted as it moves from their server to yours.
That is, if your business is just you.
The best way to get your employees buy-in on your cybersecurity plan is to design it collaboratively with them.
Involving them in the plan will increase their motivation in implementing it.
Your staff members are also the experts in your business, in its weaknesses as well as its strengths.
Start holding regular training sessions with your staff on cybersecurity issues.
This is the place to methodically work through important security techniques, like the ones we have outlined above.
verify that they do not leave passwords lying around on physical sticky notes or sitting on their desktop.
Make these guidelines easy to understand and follow.
Weve created a printout that includes simple steps your employees can take to stay secure.
you’re free to even have cybersecurity elements written into staff contracts.
Above all, remember that cybersecurity threats are constantly morphing and changing.
All we ask is that you attribute it to us.
We want to keep businesses safe, and your help to spread the word is important.
Click here toshare it on FacebookorTwitter.
Your data is exposed to the websites you visit!
Visit ExpressVPN
c’mon, comment on how to improve this article.

