Summary
Love or hate cryptocurrency, there is an awful amount of money involved.
Ponzi scheme scams have made their way into cryptocurrency and are now one of the most damaging scams.
The organizers devise a seemingly convincing reason, such ascrypto arbitrageactivities, to explain how they generate the returns.

Once investors join the program, they are asked to recruit more affiliates to increase their earning potential.
At some point, the pyramid scheme becomes unsustainable and collapses.
ICOs are used by cryptocurrency companies to raise money from future users.
While many great companies have been built using ICOs, many fundraising exercises have turned out to be scams.
ICO scams spend months promoting their fundraising exercises despite not having functional products or services.
They employ different techniques, including offering bounties for guerrilla marketing, raising money, and making enticing promises.

Then, once they’ve raised enough funds, they cease all communications with their investors.
Many ICOs seem to be operated by legitimate entrepreneurs with good track records.
Some projects go as far as getting the public support of reputable names in the industry.
It’s often difficult to distinguish between a legitimate and fake ICO.
This is partly because ICOs are carried out online without face-to-face interaction between the organization and stakeholders.
Furthermore, even legitimate ICO projects can lose investor money if they get hacked!
Everything can be done online.
Once they’re done and ready, they start pumping the assets to their followers on social media.
Would be investors buy the token, pushing the token’s price further.
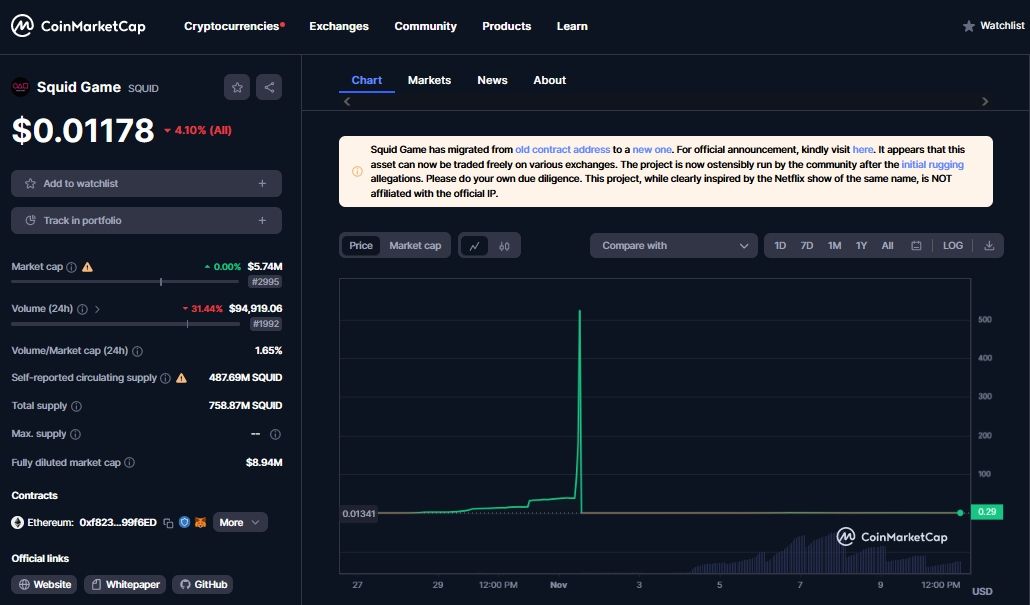
A good example of apump-and-dump scam is the Squid Game token.
According toChainalysis, crypto investors lost $4.6 billion buying into suspect pump-and-dump tokens in 2022
4.
Bitcoin Mining Scams
Over the years,Bitcoin mininghas become much harder to carry out.
This makes people more willing to outsource cryptocurrency mining to others.
Consequently, scammers have taken advantage of people’s willingness to employ cryptocurrency mining services.
The scammers usually stop responding to their victims' messages after receiving the funds.
Impersonation Scams
Impersonation crypto scams come in all shapes and sizes but follow a standard sequence of events.
The scammer pretends to be someone they are not.
They interact with potential victims, employing social engineering tactics.
Senior citizens are especially vulnerable to such scams due to their unfamiliarity with the digital space.
TheFBI IC3 unitreported over $1 billion in losses for American senior citizens in 2022.
They continue to solicit more money until the victim catches on, and then they disappear.
During the non-fungible tokens (NFT) craze, NFT giveaway scams were especially popular.
Such scams can be quite convincing, especially when scammers impersonate celebrities to persuade their victims.
Twitter accounts have also been used to steal money from people expecting cryptocurrency giveaways.
Criminals impersonate celebrities and high-profile figures in the technology industry to gain the trust of users on the platform.
In this case, scammers create full-fledged websites that represent or look similar to legitimate crypto platforms.
They then trick investors into connecting their crypto wallets to perform crypto transactions.
The hackers can gain access to cryptocurrency wallet users' data once they obtain their exchange and wallet information.
Airdrop scams use fake websites and DApps to conduct their activities.
Also, other scammers can use fake websites to prompt users to download software.
Yield Farming Incentives
Yield farmingis a decentralized finance innovation that makes earning returns from staking cryptocurrencies possible.
Yet, not all yield farming projects are legitimate.
Some are out here to steal from you.
Crypto scammers copy the code of legitimate yield farming projects and add their malicious code to steal funds.
The faceless nature of the yield farming ecosystem makes it very difficult to ascertain whether a project is legitimate.
Data leaks and privacy-averse user agreement policies have become prevalent in recent years.
The email could contain a description of an issue requiring immediate attention.
Cryptocurrency technology has automated many financial processes and put banking in the hands of the people.
Therefore, you should always scrutinize any crypto platform before using it.