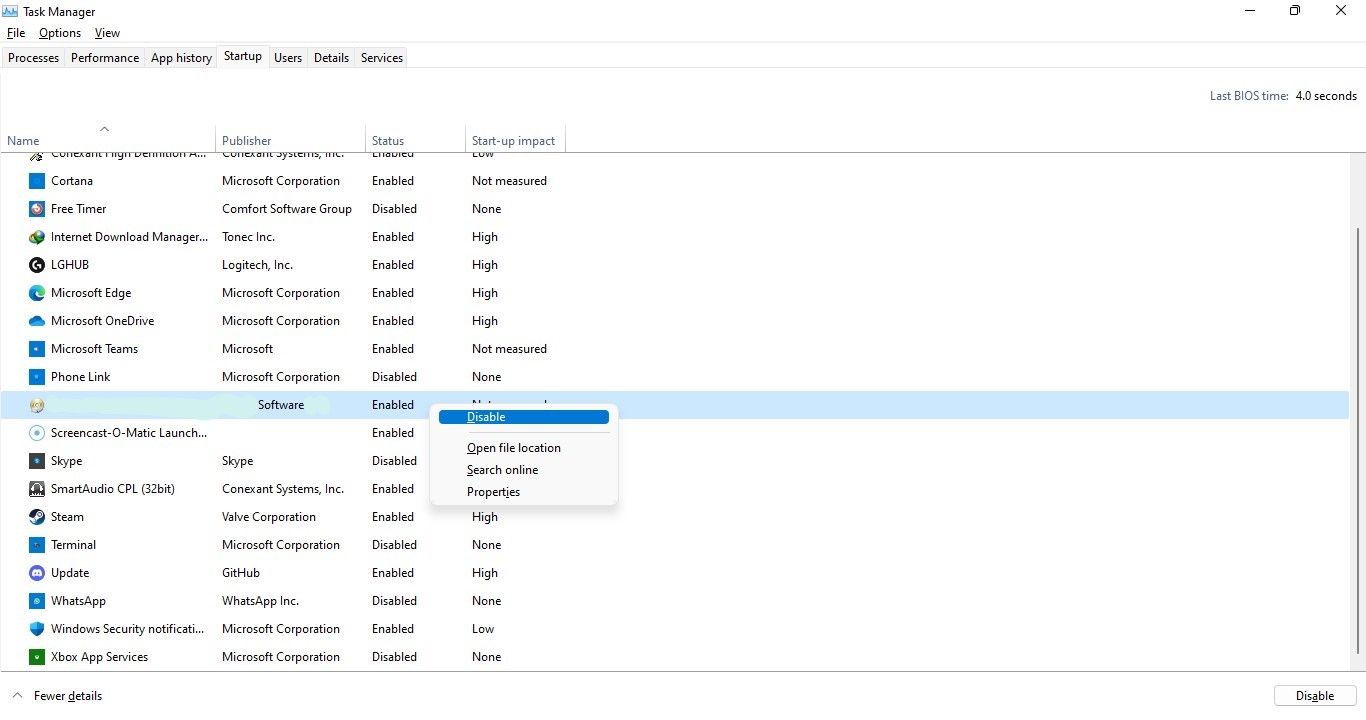
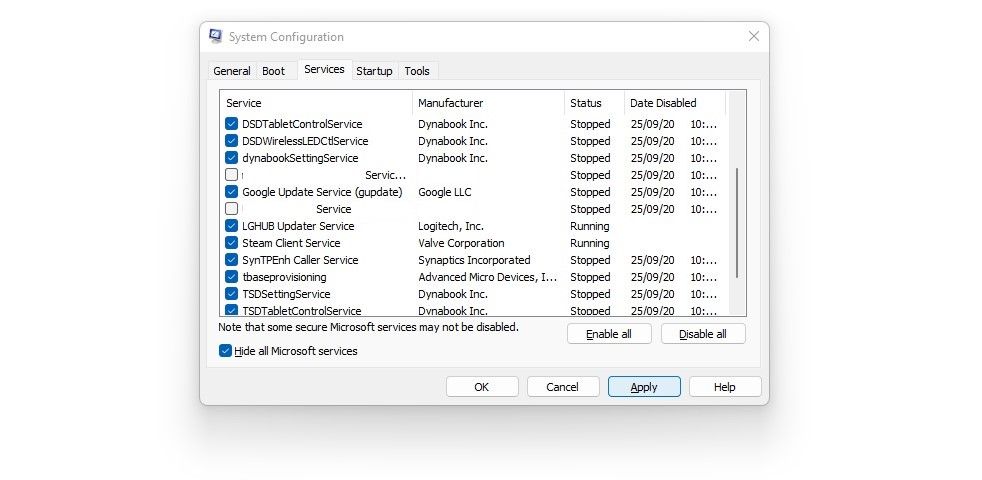
The viruses often alter your system tweaks, making it easier for them to re-infect the machine.
Let’s get started.
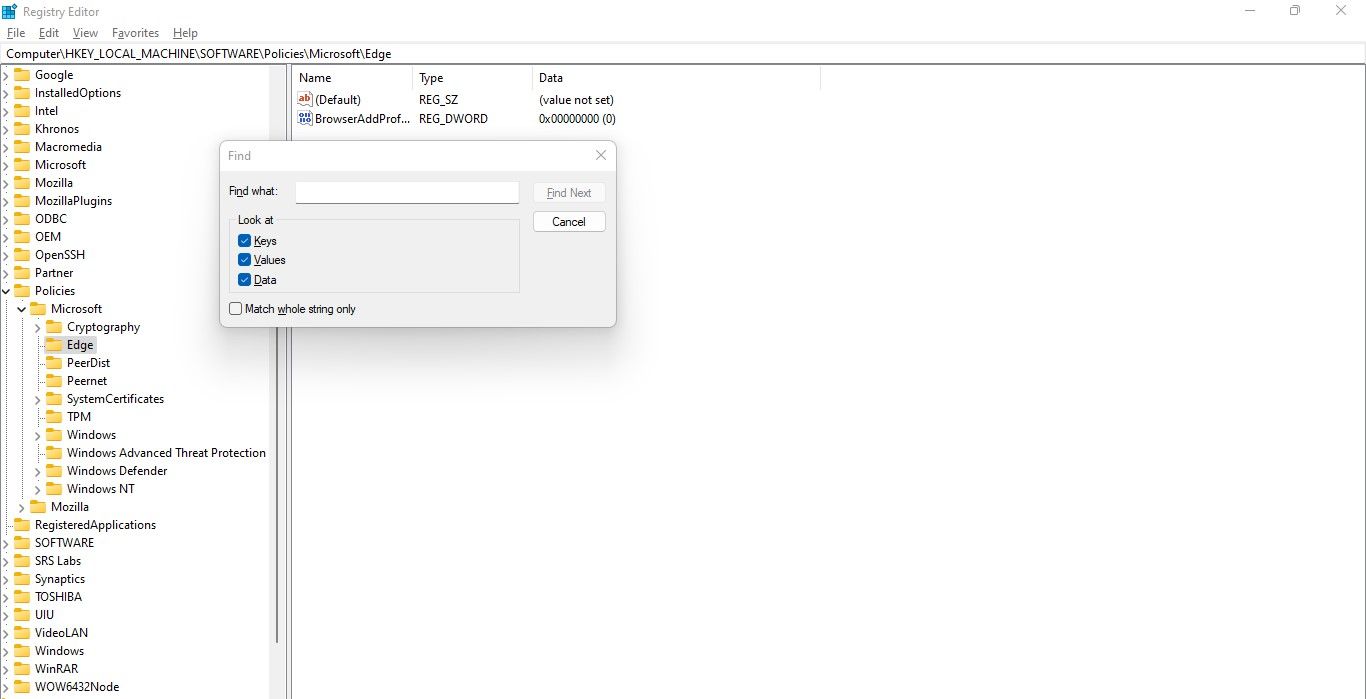
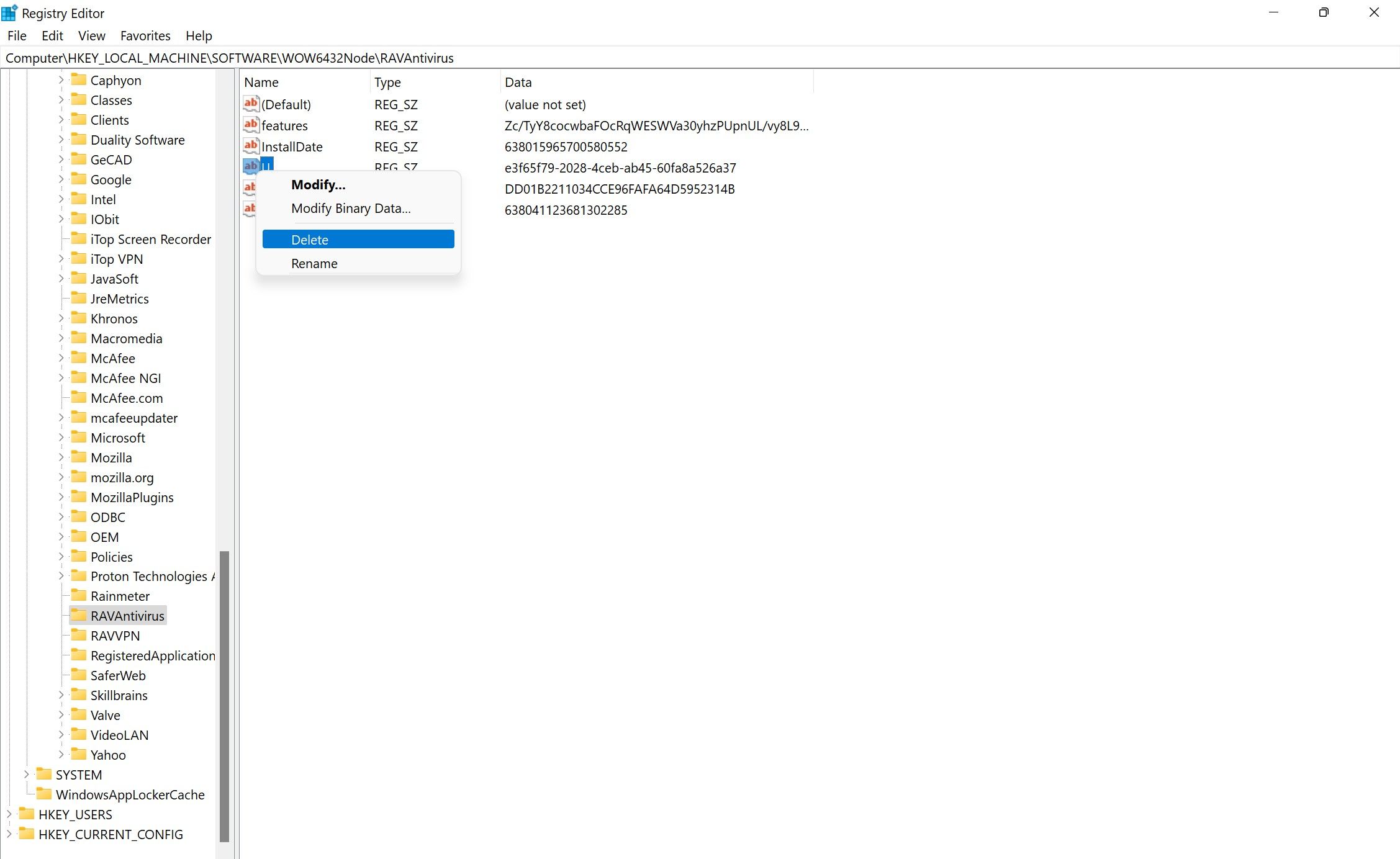
Therefore, you will have to undo the changes from scratch again.

after you grab confirmed that, you better undo the changes.
As a result, any changes made after that are automatically reverted.
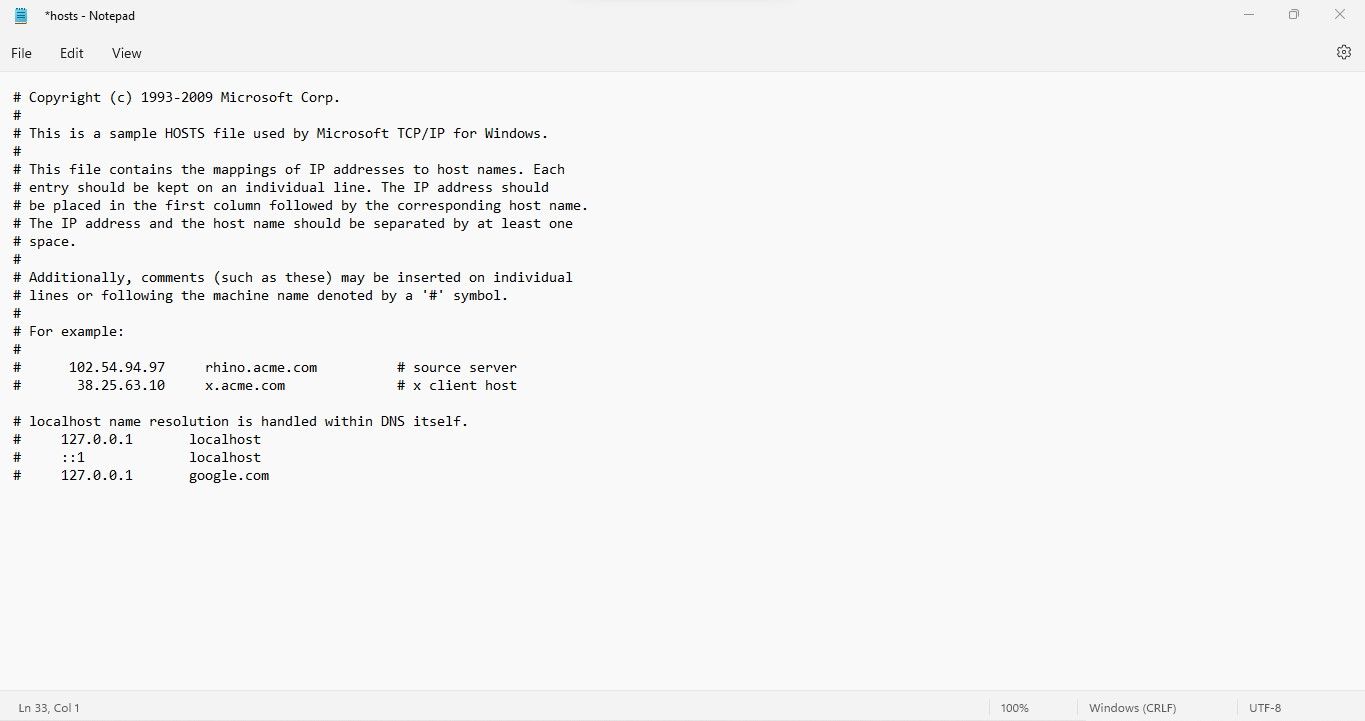
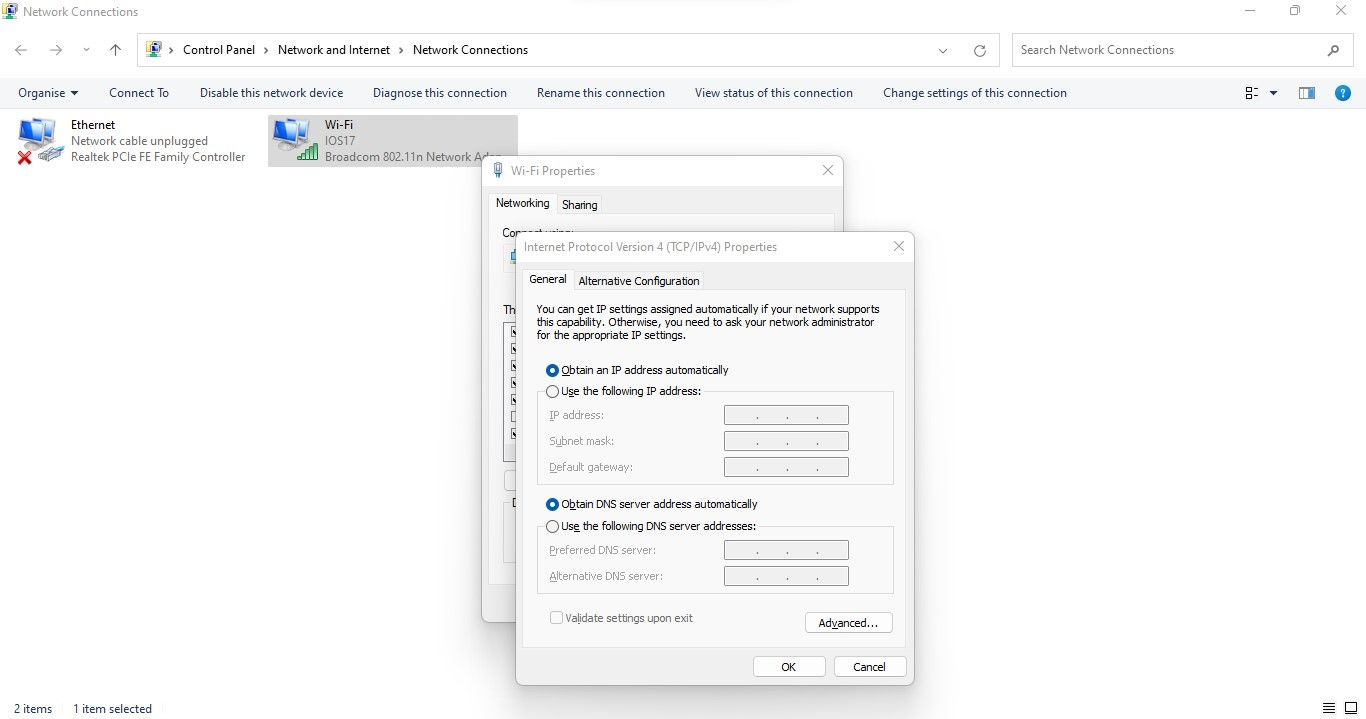
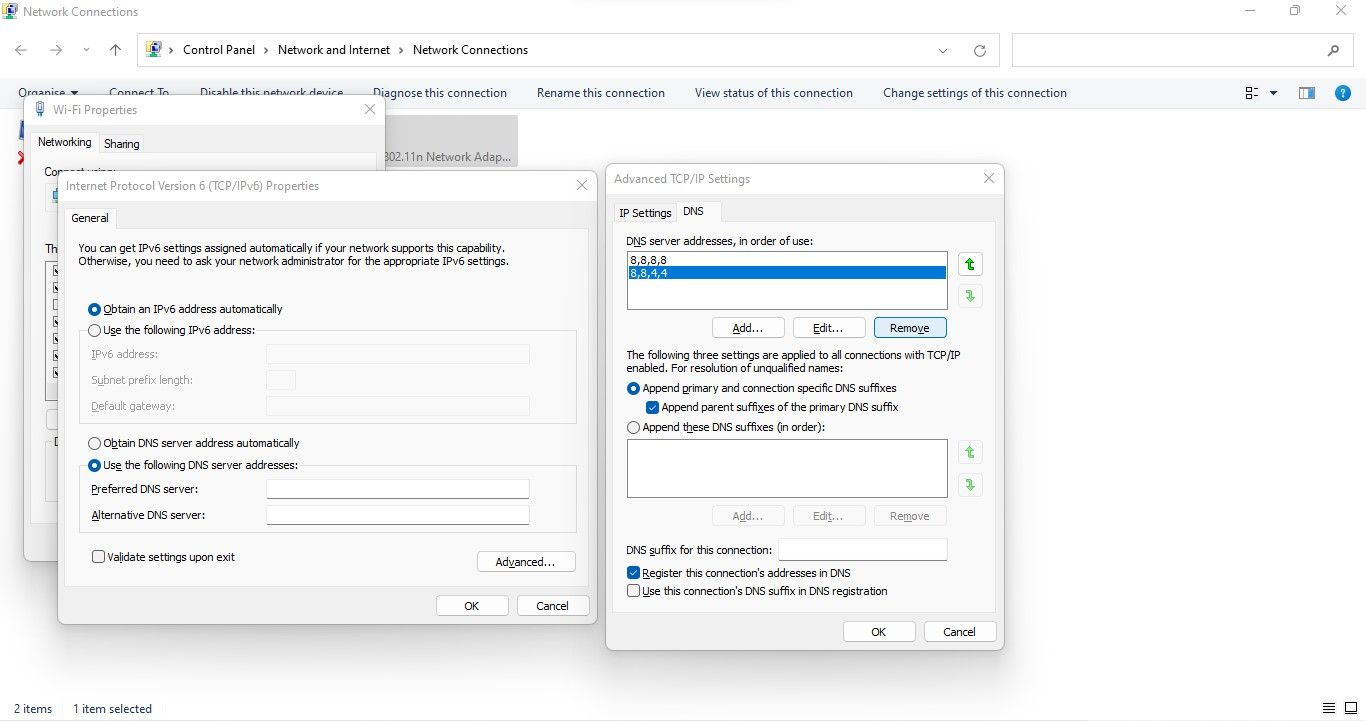
Hence, you should first check to see if the Hosts file has not been hijacked.
Because fake websites look and feel the same, you could easily be fooled.
Regardless of what the hijacker is called, the same instructions apply.
Ending the wrong processes can cause a system crash.