The online world can feel like the Wild West.
With digital threats lurking at every corner, it’s easy to feel vulnerable.
Enter ethical hackers our very own cybersecurity sheriffs.

Year after year, ethical hackers continue to uncover an increasing number of software vulnerabilities.
In this article, we’re diving deep into the captivating world of ethical hacking.
Jump to the articlesGlossary of Termsfor definitions of some of its technical language.

This introductory section looks at the history, evolution, and key milestones of ethical hacking.
As computing grew in popularity, “hacking” also referred to computer enthusiasts pushing technological boundaries.
Today, “hacking” describes exploiting computer system vulnerabilities for unauthorized access.

Such actions are illegal and have severe repercussions for perpetrators who are caught.
The term now covers both innovative technical skills and illicit cyber activities.
Why Does Ethical Hacking Exist?

The primary goal is to identify vulnerabilities and strengthen defenses.
Some ethical hackers arent formally authorized to assess a companys vulnerabilities.
They aim to report any found weaknesses to the respective companies, contributing to consumer safety.

The role of ethical hacking has become crucial in recent years, paralleling the rise in cybercrime.
Hacking and Cybercrime Legislation
4.
Popular Ethical Hacking Techniques
One of the primary techniques ethical hackers use ispenetration testing.

In this, authorized professionals pinpoint and exploit vulnerabilities by mimicking real-world cyberattacks on computer systems.
In this way, they help organizations proactively detect weak spots, helping close off potential entryways for cybercriminals.
Other popular techniques include:
6.

This timeline captures the evolution of hacking from a subculture hobby to a recognized profession essential for global cybersecurity.
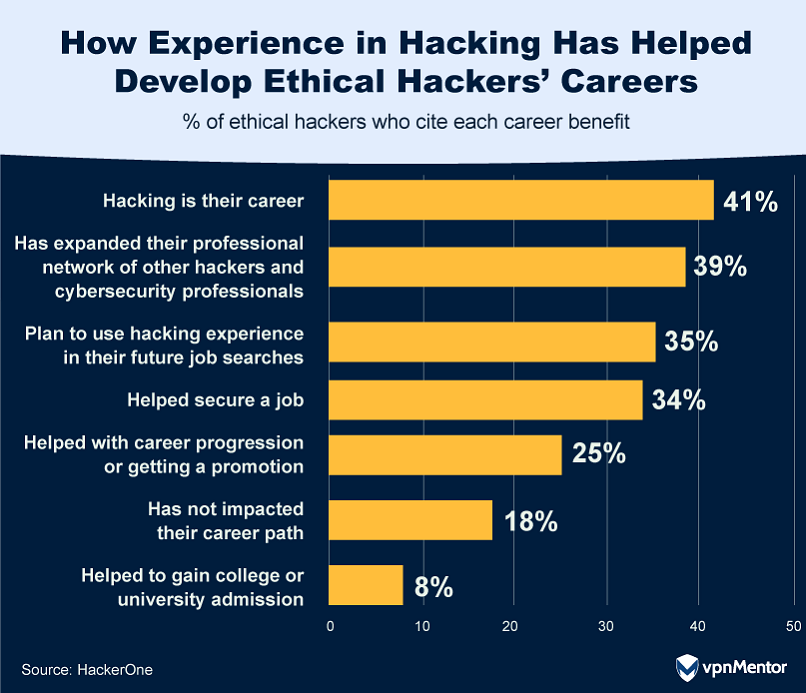
What Motivates Ethical Hackers?
Ethical hackers have varied reasons for what they do.

80% are driven by the potential earnings, which is up from 71% in 2022.
Which Industries Use Ethical Hackers the Most?
The pharmaceutical industry, for instance, accelerated its adoption of ethical hacking programs by a remarkable 700%.

The automotive industry wasnt far behind, registering a 400% growth.
What Tools Do Ethical Hackers Use?
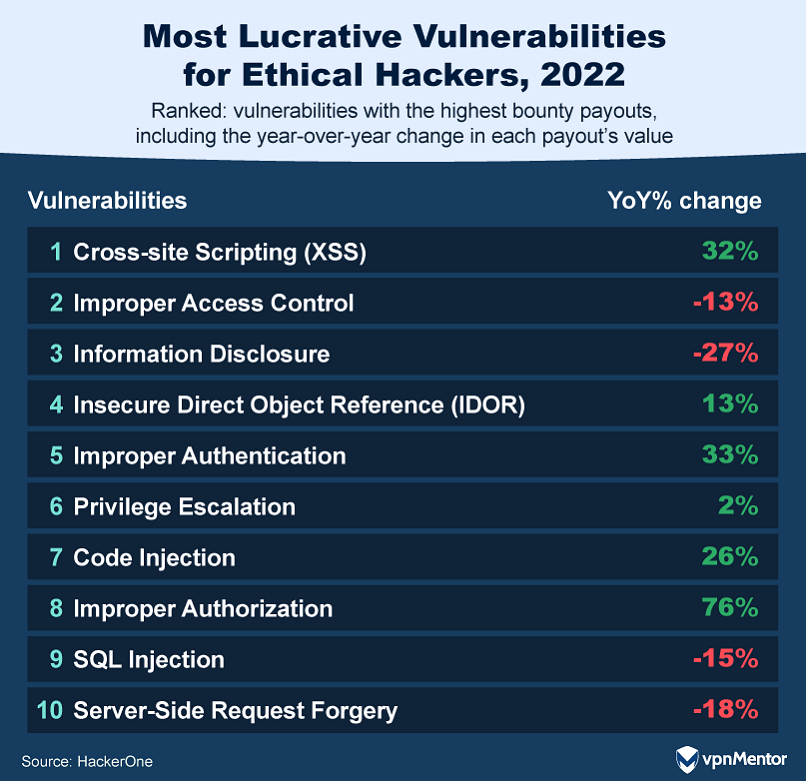
How Many Vulnerabilities Do Ethical Hackers Find?

A whopping 92% of ethical hackers believe they can spot online weaknesses that computer programs miss.
In 2022, they found over 65,000 issues that could have affected customers.
This shows just how vital human expertise remains, even in our tech-driven world.

Yet, a surprising 50% of hackers opt not to share their findings.
The leading reason, at 42%, is straightforward: Many organizations lack a formal vulnerability disclosure program.
Additionally, 12% of hackers are deterred by intimidating legal language on program pages.
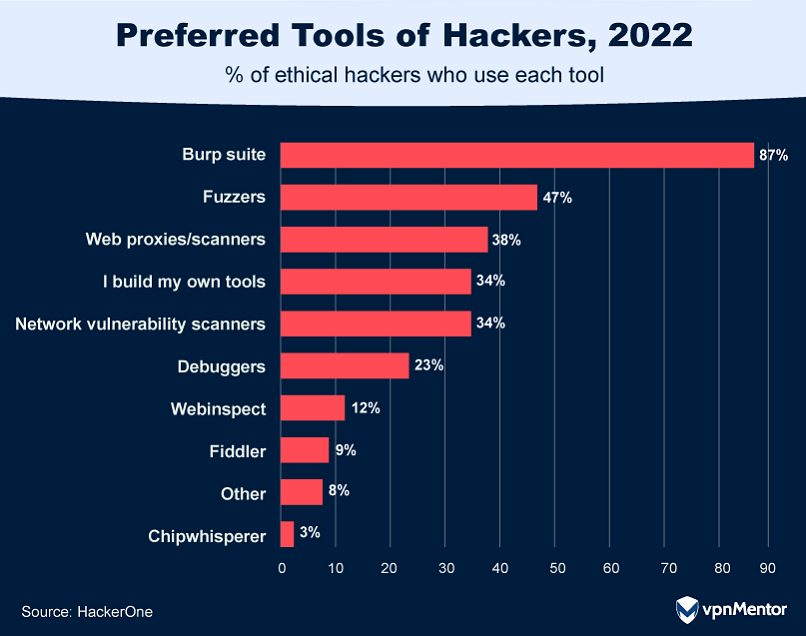
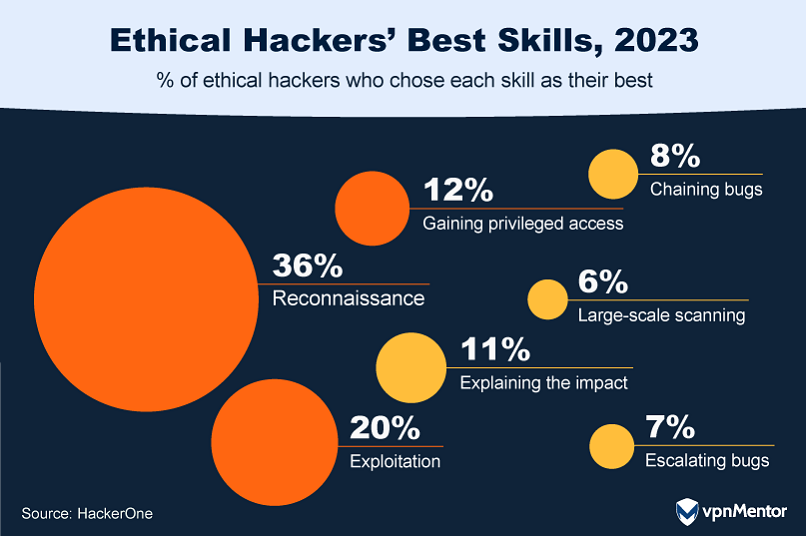
What Specialized Skills Do Ethical Hackers Have?
They simulate attacks to reveal the potential impact of a real-world breach.
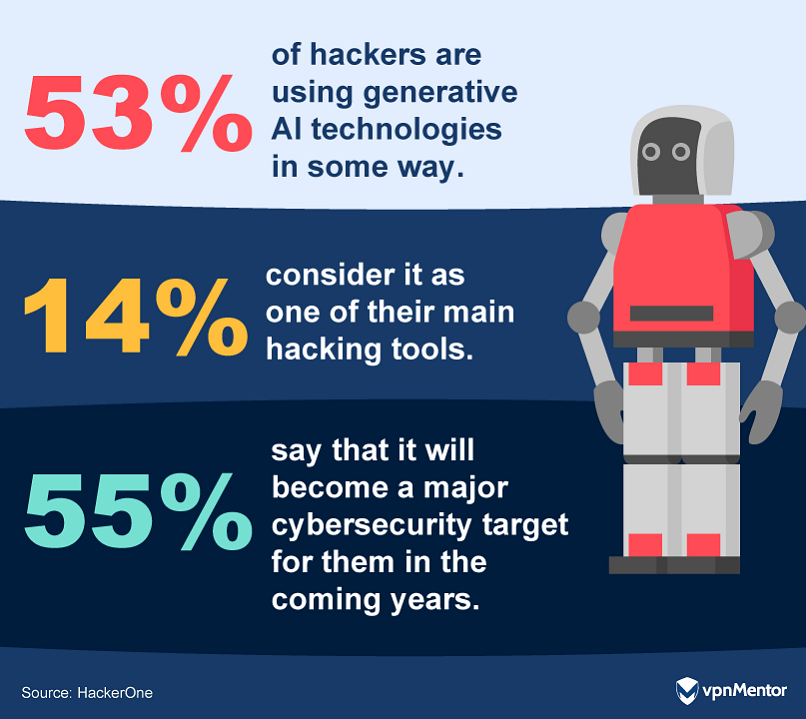
However, with the adoption of GenAI, new challenges emerge.

A substantial 55% foresee GenAI tools themselves becoming major targets.
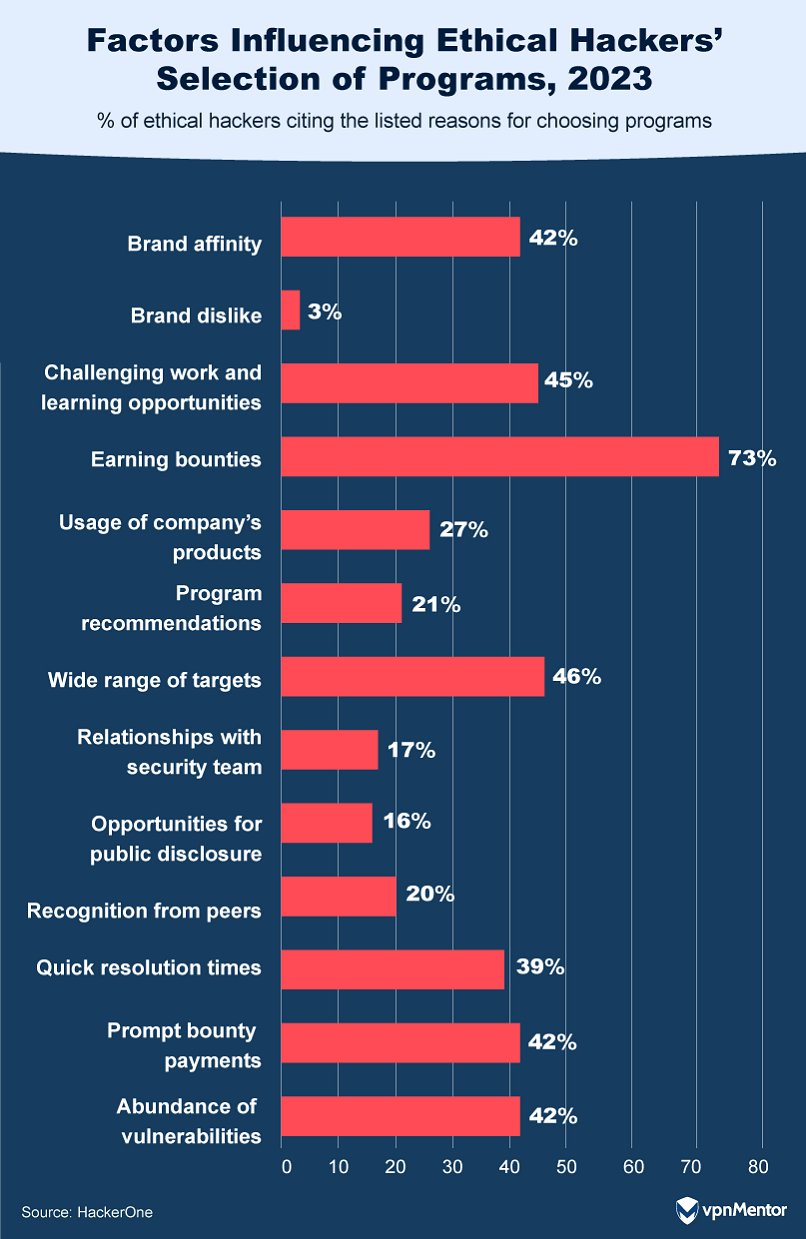
What Draws Ethical Hackers to Specific Programs?
When it comes to selecting their targets, ethical hackers have clear preferences.
The allure of bounties stands out, with 73% of hackers gravitating toward programs offering the best rewards.
Brand affinity also plays a role, influencing 42% of hackers in their choice.
But lesser-known brands can still attract and benefit from ethical hackers.

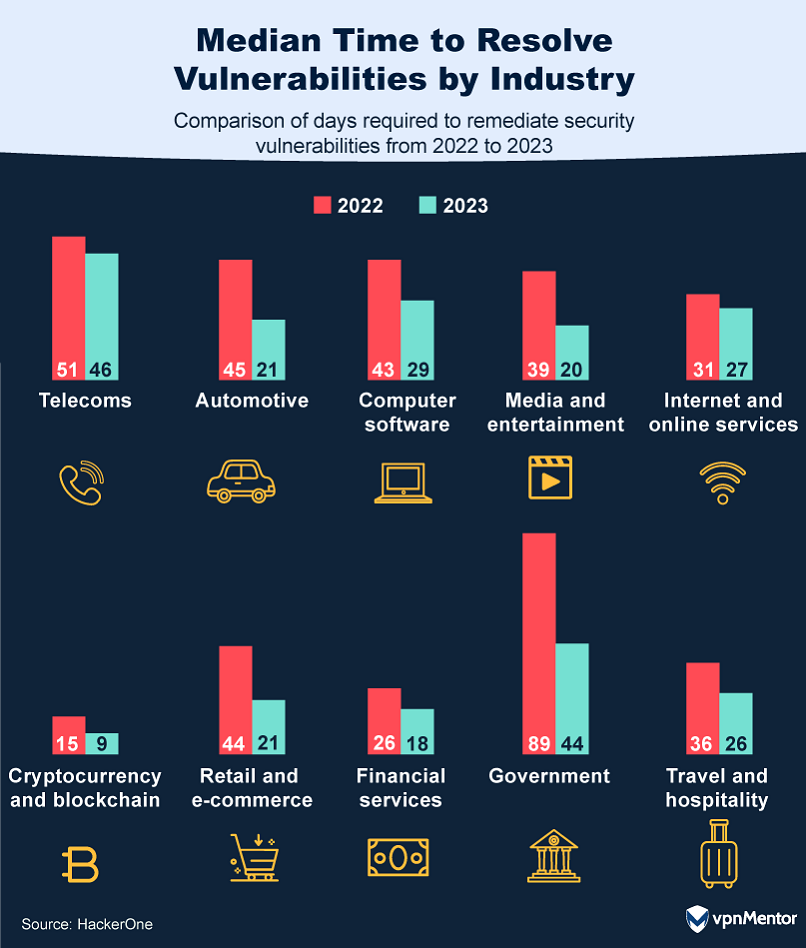
Government agencies decreased from 89 to 44 days, underscoring a concerted effort to resolve risks more quickly.
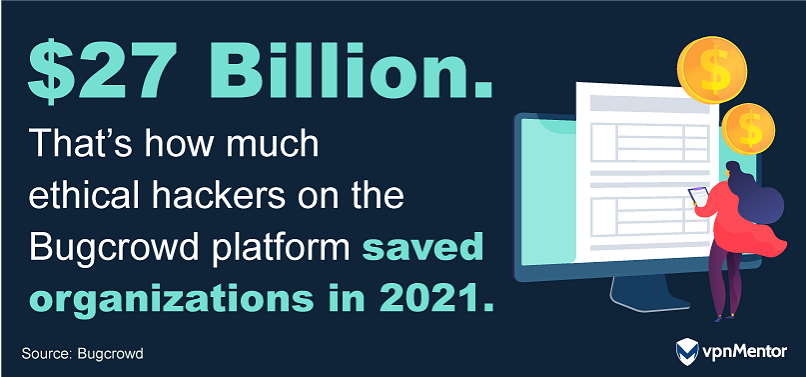
How Much Money Do Ethical Hackers Save Companies?
This figure represents the efforts of the 59% of ethical hackers who are part of the Bugcrowd community.
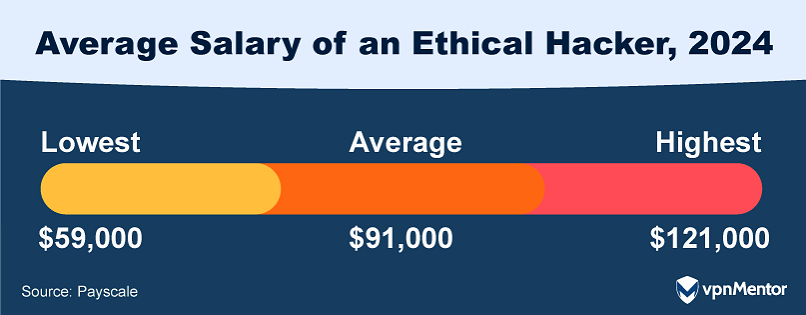
How Much Do Ethical Hackers Make?
Ethical hacking is both an essential component of cybersecurity and also a lucrative career path.
As of 2024, the median annual salary for ethical hackers stands at approximately $91,000 according to Payscale.

Meanwhile, top-earning ethical hackers can make well over $100,000.
This makes it the fifth fastest-growing occupation in the economy.
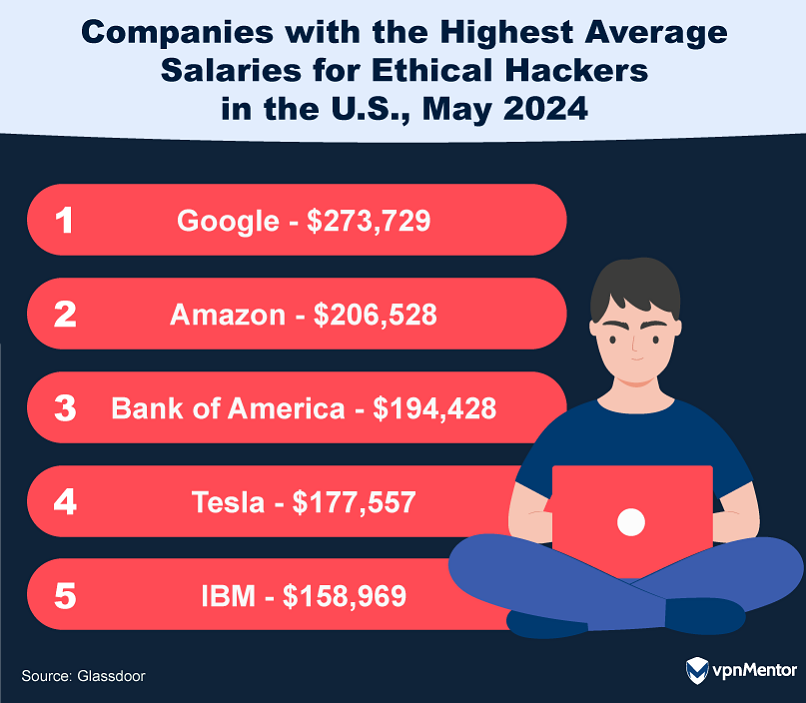
Bank of America, Tesla, and IBM are also strong contenders.
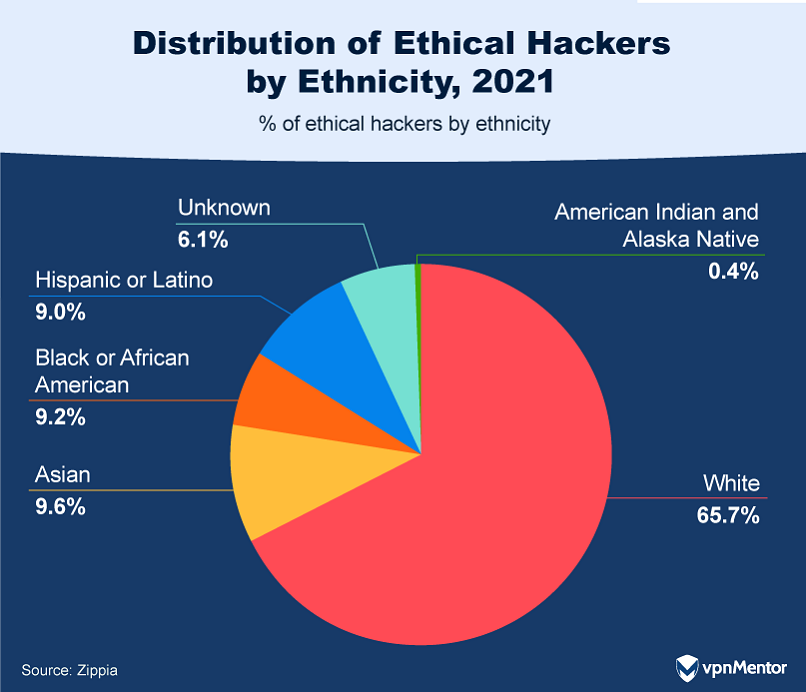
Ethical Hacking Demographics
In the realm of ethical hacking, demographics shape perspectives and influence the landscape.
This section explores how an ethical hackers background impacts their roles and contributions.
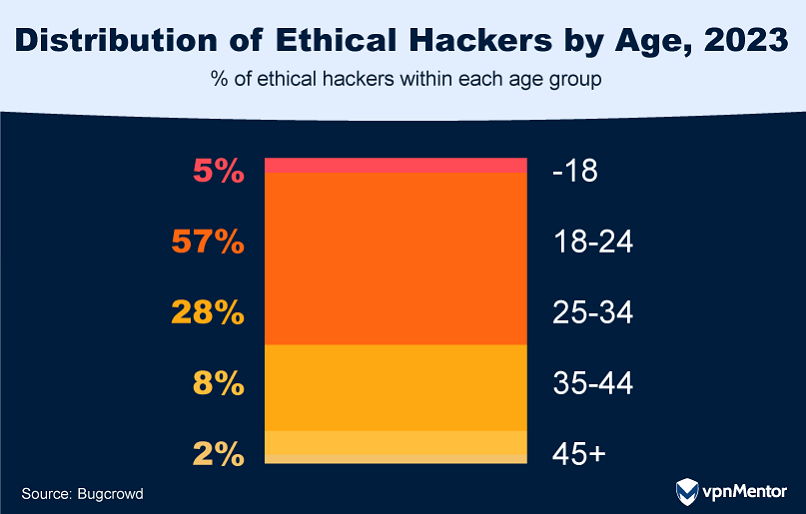
How Old Are Ethical Hackers?
The world of ethical hacking is getting younger.
Most ethical hackers are now from Gen Z, the group of people born between 1997 and 2012.
They’re followed closely by Millennials, who were born between 1981 and 1996.
What’s interesting is that the number of hackers under 18 has more than doubled in the last year.
This shift highlights a positive trend toward greater diversity within the ethical hacking field.
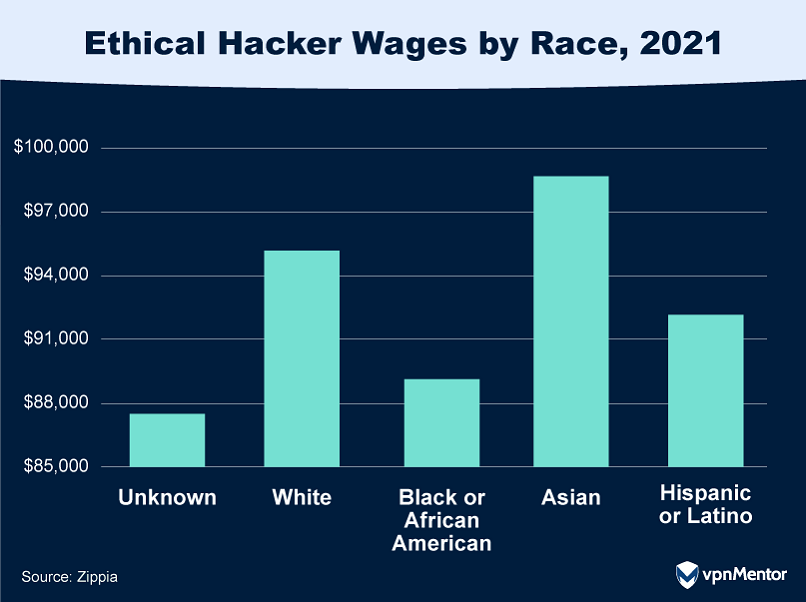
This is closely followed by white hackers earning $95,174, and Hispanic or Latino hackers at $91,847.
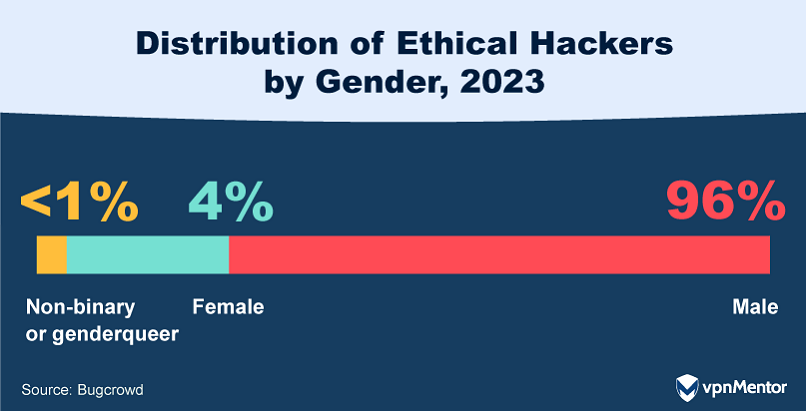
This marks a decline in female representation from 2020 when 6% of hackers were female.
The pandemic’s added pressures, such as increased childcare responsibilities, may have contributed to this decline.
This gender disparity threatens the diversity and range of perspectives that make crowdsourced security so effective.
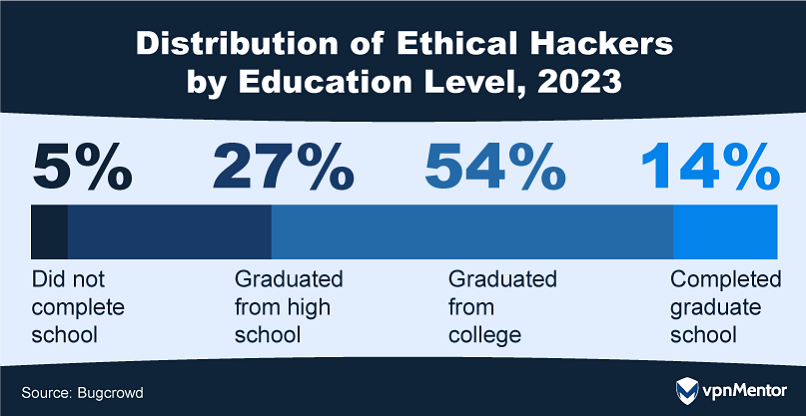
A majority of 68% of hackers are college graduates, highlighting that this community is well-educated.
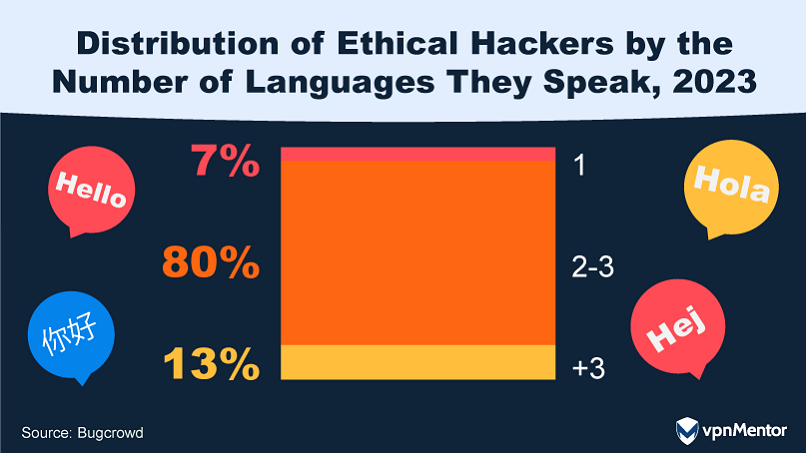
Studies show that hackers from non-English speaking countries are increasingly using AI technologies like ChatGPT as translators.
Where Do Ethical Hackers Call Home?
Penetration Testing
Penetration testing serves as a fundamental tool in identifying and fortifying against potential cyber threats.
This robust growth underscores the increasing recognition of pen testing’s role in bolstering cybersecurity defenses.
Average Cost of a Penetration Test
Calculating the costs of penetration testing can be complex.
They average $18,300 but can start as low as a few hundred dollars and exceed $100,000.
They vary widely depending on thefocusandmethodology.
The year saw 15,851 job openings in the field.
In early 2024 alone, companies listed 4,800 job openings.
Positions range from Penetration Testers and Vulnerability Analysts to Information Security Analysts and Cloud Security Engineers.
Finally, confidence in security measures has dropped by 15%.
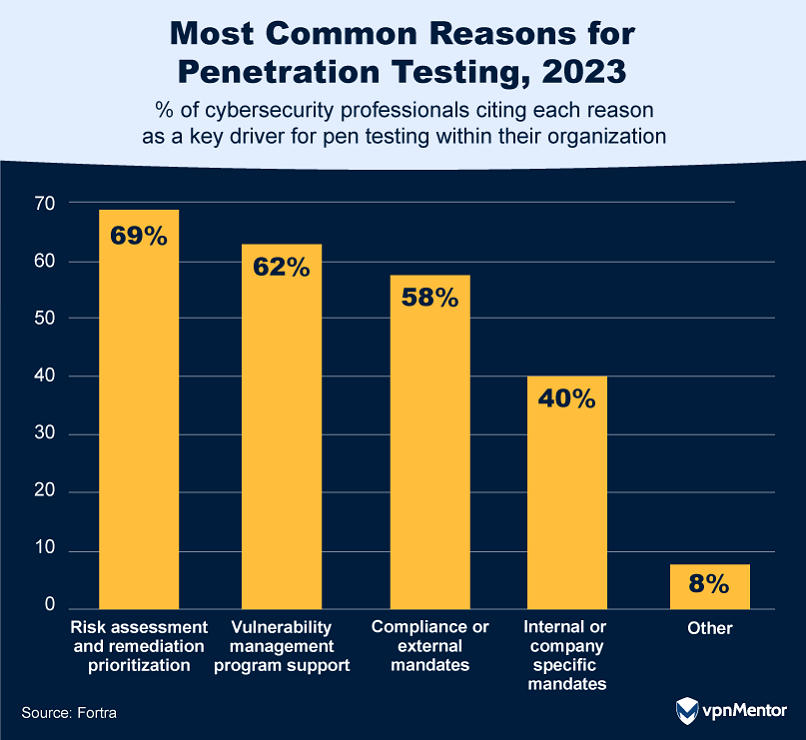
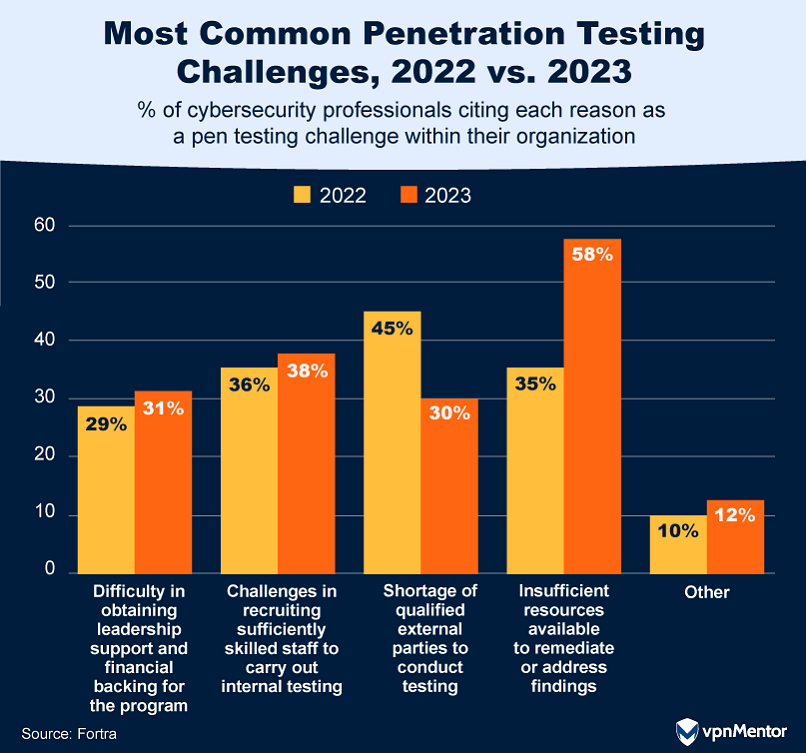
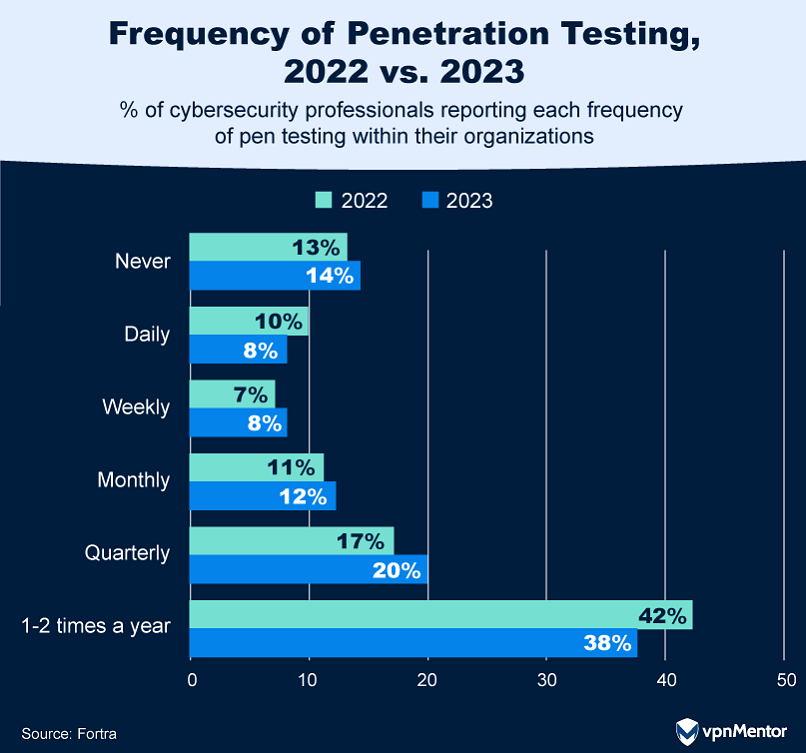
How Often Companies Really Pen Test
The frequency of penetration testing among organizations reveals some interesting trends.
Most organizations conduct pen tests only once or twice per year.
Companies that test monthly or every three months seem to have found a good middle ground.
They’re doing enough tests to stay safe but not so many that it becomes a burden.
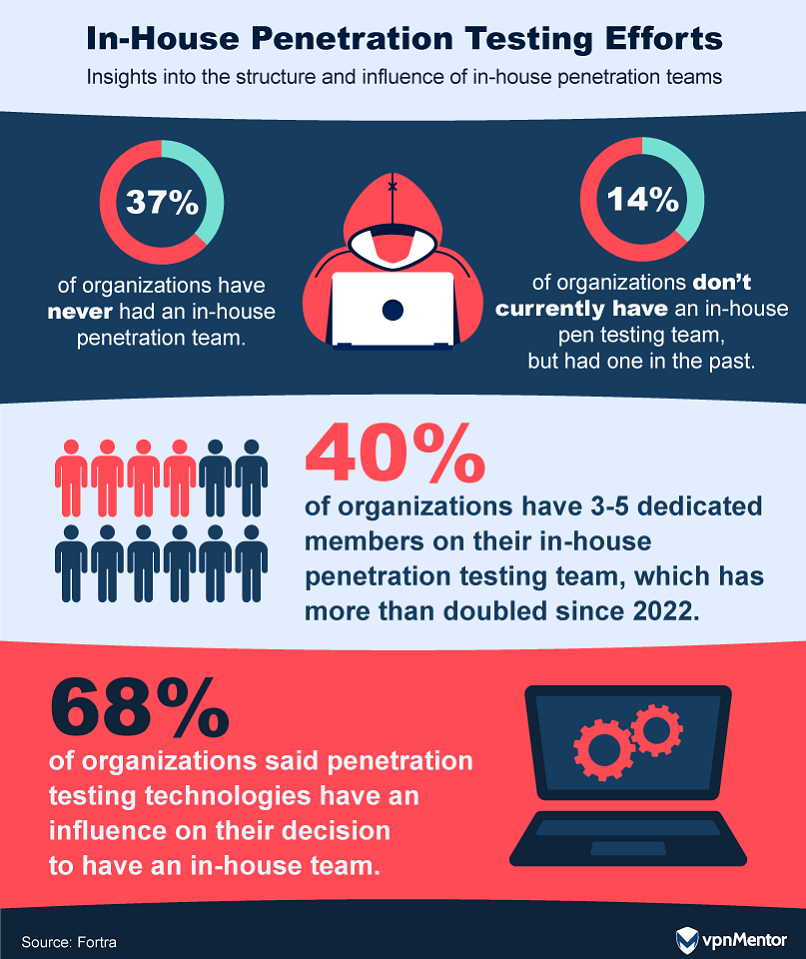
But there’s a growing trend to also do this testing with in-house teams.
The best approach seems to be a mix of both.
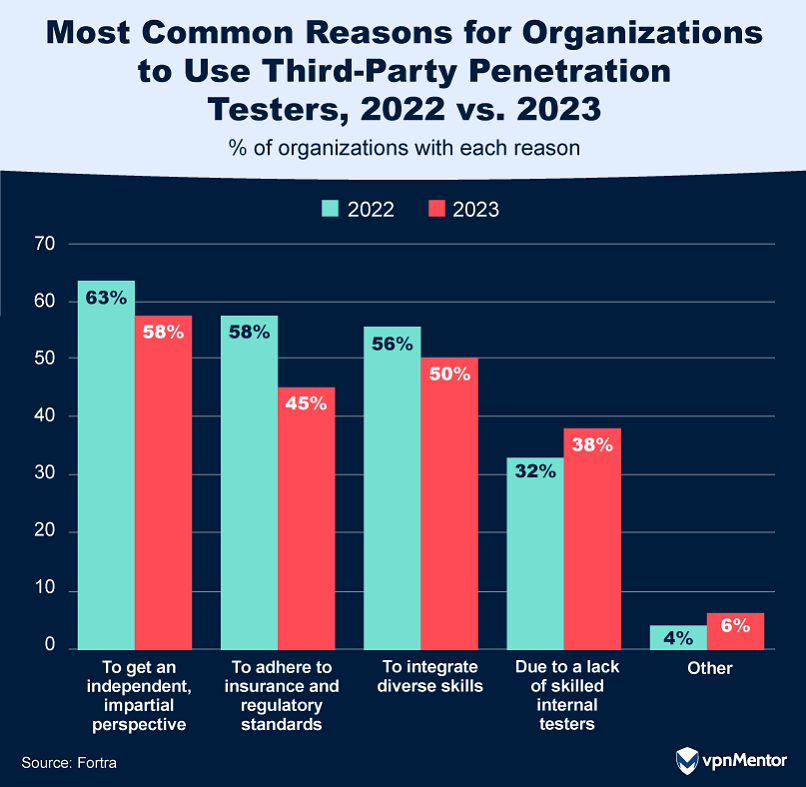
External teams offer a fresh, unbiased look at security, which is the top reason companies hire them.
They also bring specialized skills to the table.
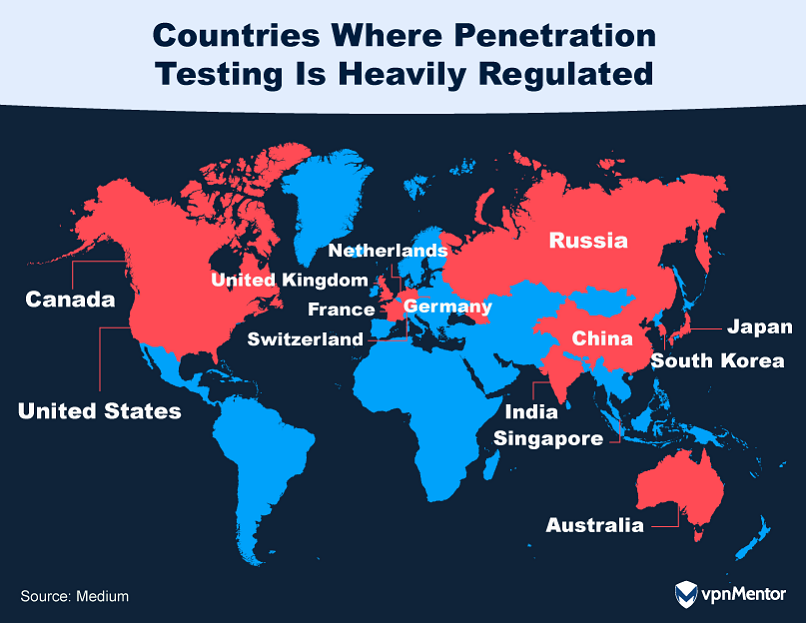
Countries like India, Singapore, and Australia also have stringent regulations requiring prior authorization.

Even in countries like China and Russia, where cybersecurity is state-controlled, explicit permissions and licenses are mandatory.
Bug Bounties
Bug bounties offer ethical hackers a compelling incentive for uncovering digital vulnerabilities.
These bounties are often facilitated through specialized platforms designed to manage such programs.
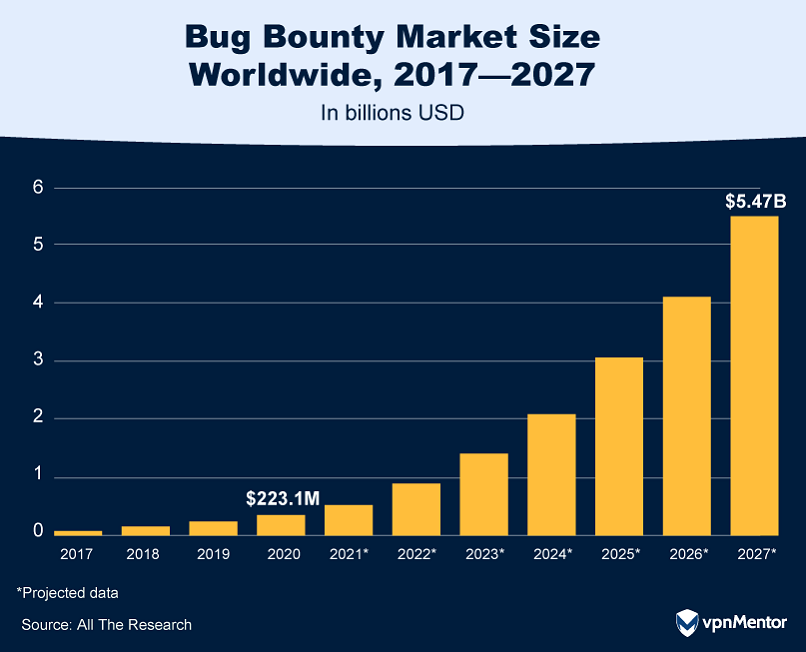
Amid a sluggish global economy, consumer price sensitivity could also play a role in shaping this burgeoning market.
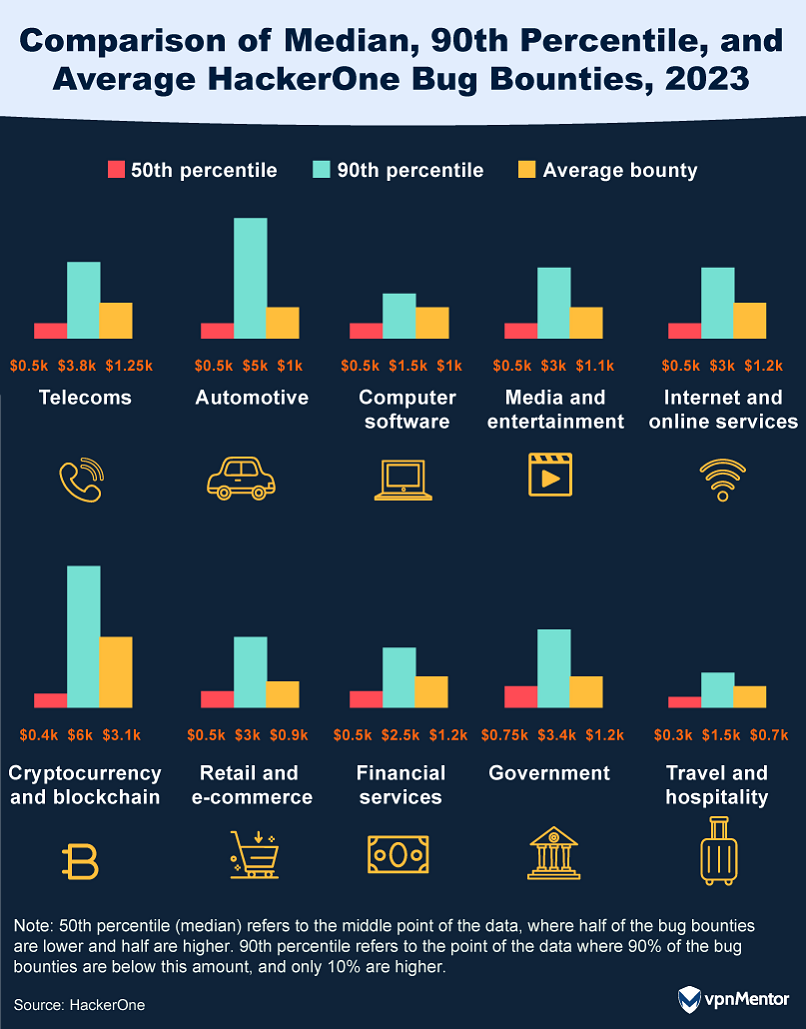
Which Industries Have the Highest Bounty Payouts?
This newfound interest wasn’t limited to the pandemic; the hobby has stuck.
Of these, over 8,500 were deemed significant enough to warrant a bounty.
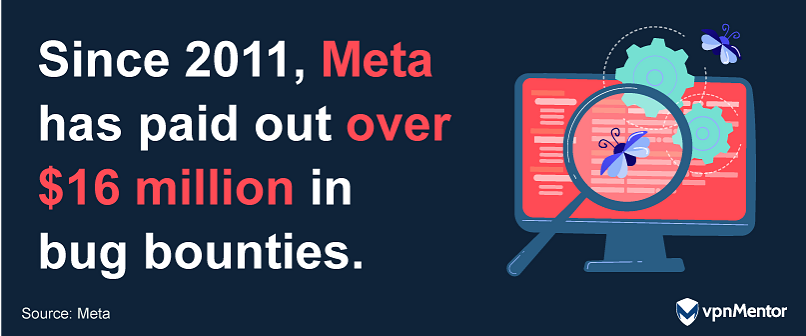
In 2022 alone, Meta awarded more than $2 million to researchers hailing from 45 different countries.
The company saw around 10,000 reports, with bounties issued on more than 750 of them.

The leading countries in terms of bounties awarded in 2022 were India, Nepal, and Tunisia.
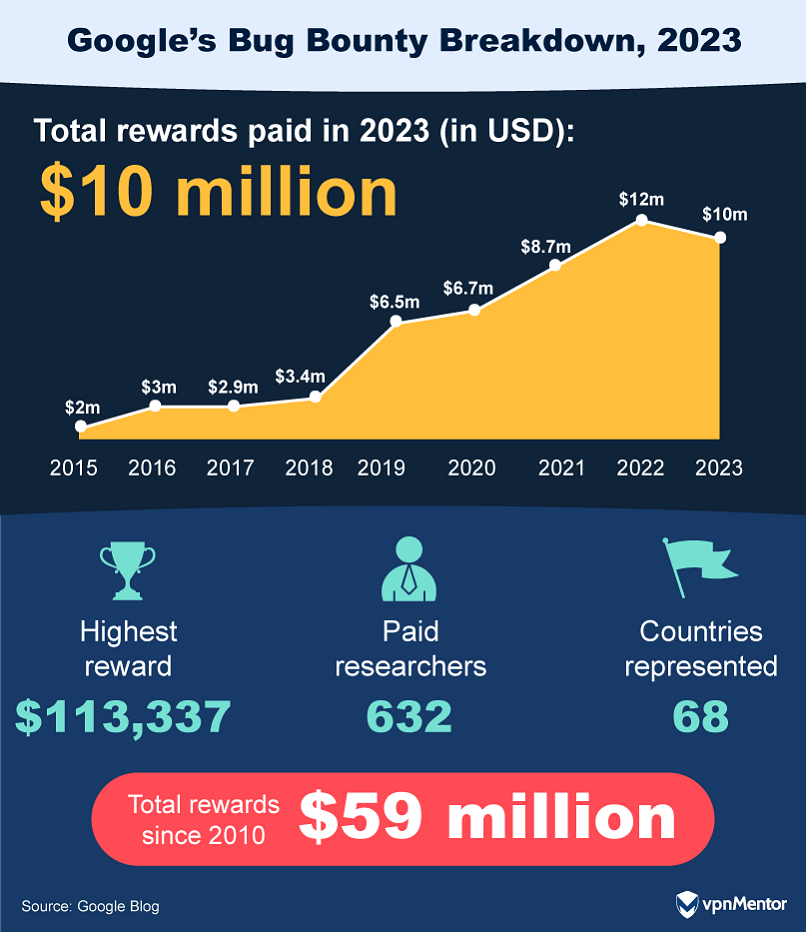
The Android ecosystem alone accounted for $3.4 million of these rewards.
The inclusion of Wear OS in the VRP incentivized further research into wearable technology.

Today, ethical hackers are recognized and even celebrated for their critical role in safeguarding digital infrastructures.
Glossary of Terms
yo, comment on how to improve this article.